Key Takeaways:
- For tech founders, taking a company public can provide significant benefits like increased capital, visibility, and liquidity, but the process is complex and comes with risks, such as increased regulatory scrutiny and reduced control.
- There are several common pitfalls to avoid during the IPO journey, including underestimating timelines, not building a strong financial foundation, and not having the right leadership in place.
- Tech companies should focus on a few things to facilitate post-IPO success as a public entity: investor relations, internal controls, and cultural shifts. These maintain trust and compliance across the board.
~
For many tech founders, the prestige and promised rewards of taking a company public are strong motivators to pursue an initial public offering (IPO).
But IPOs, however attractive, are extremely complicated and can be overwhelming — especially if you’re not a transaction expert and have never navigated the full process. Without the right information, tech founders are liable to experience delays, derailments, and disappointments on their road to an IPO.
Are you a tech founder looking to IPO for the first time? Read our guide to understand what the IPO process looks like for tech companies like yours — and what pitfalls you’ll need to avoid along the way.
Should You Go Public?
While an IPO can be a great avenue to grow your business, it isn’t the right strategy for every company — or every founder. To make an informed decision, you need to understand the benefits and drawbacks of pursuing an IPO.
Benefits
- Increased access to capital. An IPO can offer a massive influx of capital, enabling substantial, accelerated growth.
- Greater visibility. Going public can improve a tech company’s market visibility and credibility, which can in turn improve brand reputation and recognition.
- Increased liquidity for shareholders. An IPO allows early investors to cash out, while stock options remain an incredibly attractive incentive for many employees, even during times of market volatility. The stock options unlocked by an IPO can be key to attracting and retaining top talent.
- Access to a market valuation. Being listed on the stock market means the public markets offer a valuation of the tech company, which may be seen as more objective and credible than a privately sourced valuation.
Drawbacks
- Greater regulatory and compliance requirements. Publicly traded tech companies are subject to more regulatory and compliance requirements than their privately owned counterparts, and the transition to a publicly traded company can cause compliance costs to skyrocket. Public companies also face scrutiny from regulatory bodies like the SEC. Any mistake, like a reporting misstatement, is highly public and can damage the company’s reputation — and stock price.
- Less control. Public tech companies must answer to shareholders and regulators, impacting how much control a founder will have over their company. Founders also often find they have less control over their finances after going public, as the IPO process can “lock up” their cash.
- Vulnerability to market volatility. Market conditions and other external factors can cause stock prices to fluctuate, whereas private company valuations are more insulated from such forces.
- Increased disclosure requirements. Public tech companies have additional disclosure requirements, which means competitors will have access to more information about the company. This dynamic could impact a company’s competitive advantage in the marketplace.
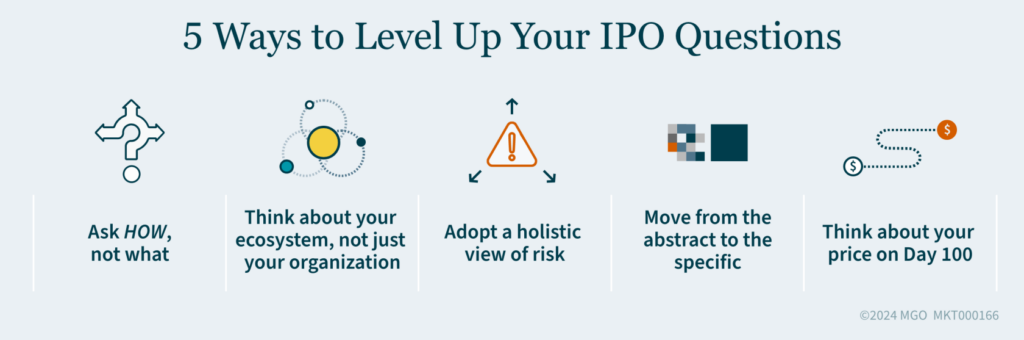
Are You Asking the Right IPO Questions?
Preparing for an IPO means investigating every aspect of your business. Asking the right questions will help you see beyond the obvious to gain an in-depth understanding of how investors will think about your company and how you can set yourself up for success throughout the IPO process.
Ready to get started?
Stage 1
IPO Readiness Assessment
A readiness assessment can help you identify gaps or issues that could prevent your organization from successfully operating as a public company. For most tech companies, the readiness assessment will uncover substantial changes required to facilitate a transition to a public company, such as implementing more robust internal controls or developing specialized accounting capabilities in house. BDO recommends clients assess readiness in the following key areas:
- Accounting & SEC reporting
- Ta
- Risk
- Technology
- Operations
- People
- Financial planning & analysis
Common Pitfalls:
- Failure to develop a compelling story. Before a leader even considers pursuing an IPO, they need to create a narrative that gets potential investors excited about the future of the company. They must define success, determine what metrics will be used to track it, and put systems in place to measure and report on progress. These steps are key to securing investor interest and confidence. Common success metrics for tech companies include annual recurring revenue (ARR), customer retention, the Rule of 40, customer acquisition costs, daily active users, and monthly active users.
- Overestimating existing resources. Tech companies often fail to understand what resources they already have and what resources they still need to secure. For example, pursuing an IPO requires specialized skills related to investor relations, treasury, income tax, technical accounting, SEC reporting, and internal controls, which most private tech companies don’t have in house. Failing to conduct a proper resource assessment can lead to a delayed IPO filing, as the company will have to make up ground and secure those resources later.
- Lack of IPO experience. As they prepare for an IPO, tech founders should prioritize building a leadership team that includes professionals who have experience taking tech companies public. IPO veterans can help guide the rest of the team through the process while identifying and addressing potential issues before they happen.
- Relying on private-company experience. Private tech company founders sometimes underestimate the depth and breadth of the requirements that come with going public. They may even make the mistake of believing that a private company approach will be sufficient post IPO. Instead of relying on what they already know, founders must continuously assess their policies, procedures, and governance structures and compare them to public-company requirements to identify and proactively address gaps.
- Failure to protect intellectual property (IP). IP is a major asset for many tech companies and can significantly impact their valuations. Before tech leaders take their company public, they must assess their current protections and deploy tactics like developing a strong patent portfolio to ensure their IP is secure.
Stage 2
Roadmap and Program Management
Once you understand your current state, it’s time to develop a roadmap to guide your transformation from a privately held company to a public company. A strong roadmap will require input from numerous people and functions across the company, as well as reasonable estimates around the time and effort required to meet your objectives. Effective program management is critical to developing your roadmap as quickly and efficiently as possible.
Common Pitfalls:
- Underestimating timelines. Tech leaders often underestimate the time needed to prepare a company for an IPO, which can take as long as 18-24 months. A successful transformation depends on a realistic and carefully planned timeline. Attempting to rush the process can lead to expensive and public mistakes like financial misstatements.
- Missing inputs. A successful IPO process relies on participation from the full organization. Failing to include specific departments or professionals in the roadmap stage can lead to process gaps that later derail progress. For example, failure to include IT in the roadmap stage can lead to errors when it comes time to upgrade or rationalize back-office technology in advance of the IPO filing.
- Lack of a change management plan. Poor change management can lead to unnecessary disruption. For example, lack of a change management plan can create employee discontent during the transition, causing the company to lose key talent and disrupting operations at a crucial juncture.
Stage 3
March to IPO
At this stage, your goal is to get ready for the IPO filing, which entails executing your roadmap to prepare your organization to operate as a public company. This is also the point at which you will begin preparing for the IPO filing process itself, including selecting an underwriter, pricing the IPO, and conducting a roadshow.
Common Pitfalls:
- Failure to build a strong financial foundation. Tech companies preparing to go public need to review their financial statements to verify they are accurate, audited, and up to date. Many tech leaders opt to review three years of financials, even if regulations allow for fewer, to help bolster investor and regulator confidence. Failure to build a strong financial foundation can delay SEC filings, which may impact filing status and result in expensive fines.
- Inadequate pro forma reporting plans. Tech company leaders must vet their post-IPO reporting plans against SEC reporting rules to ensure they will meet all relevant requirements. They must also design a comprehensive reporting process, building in checks and balances to ensure all numbers are accurate.
- Misaligning compensation structures. As tech leaders revisit their compensation structures, they must make sure that compensation plans don’t conflict with shareholder interests. For example, option-based compensation for CEOs can encourage excessive risk-taking behavior that may damage customer relationships and firm performance, decreasing shareholder value.
- Skipping the trial run. Tech companies should practice operating like a public company before filing for an IPO. This trial run can help uncover hidden or overlooked issues like a lack of uniform controls and reporting policies. Companies that skip the trial run often find themselves surprised by requirements and challenges post IPO, which can take significant time and money to address.
Stage 4
Post-IPO Support
After the IPO has been filed, it’s time for your tech company to start operating as a public company. At this stage, you need to ensure you are delivering on your promises, managing expectations with your new shareholders, and meeting your new reporting requirements as a public company.
Common Pitfalls:
- Lack of forecasting capabilities. As private companies transform themselves to prepare for an IPO, they need to adopt strong revenue forecasting capabilities. Unfortunately, newly public tech companies often struggle with revenue forecasting, which can cause investor distrust and reputational damage.
- Failure to maintain investor relations. Investor expectations will expand after going public, as shareholders await regular updates on company performance. Failing to build strong relationships with investors through proactive, comprehensive communication can breed mistrust.
- Failure to manage the cultural shift. When private tech businesses transition into public companies, a major cultural shift often follows. Failure to manage that shift correctly can lead to employee dissatisfaction and talent retention issues.
- Poor internal controls. Once a tech company goes public, it will have to comply with new reporting requirements and regulations, notably Sarbanes-Oxley (SOX). Prior to filing the IPO, the company should have all necessary internal controls in place — without them, the company may experience issues like material misstatements that can negatively impact stock price.
How MGO Can Help
There’s no question that going public is an exciting “next step” in your company’s evolution. With an IPO comes additional opportunities to transform the business, but it can also come with more challenges. MGO’s team is here to support you at every stage, from IPO planning and readiness assessments to execution and post-IPO acquisition services.
With today’s rapidly evolving technology, you want to stay at the forefront of developing products that transform how we work, think, and engage with the world. Reach out to our Technology team today to find out how we can help you achieve your goals.
Written by Hank Galligan and Jim Clayton. Copyright © 2024 BDO USA, P.C. All rights reserved. www.bdo.com