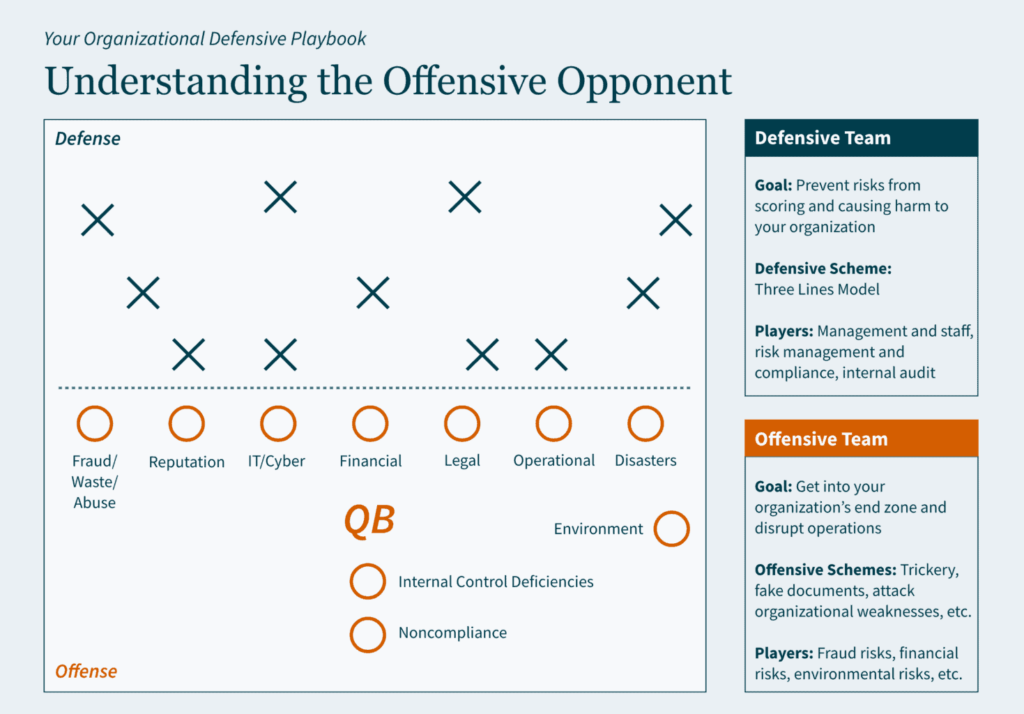
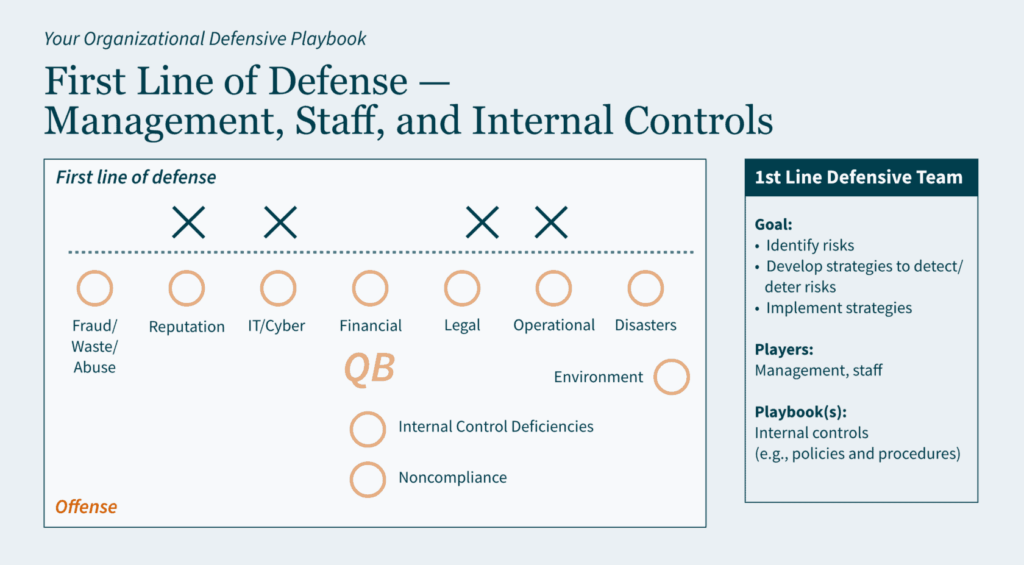
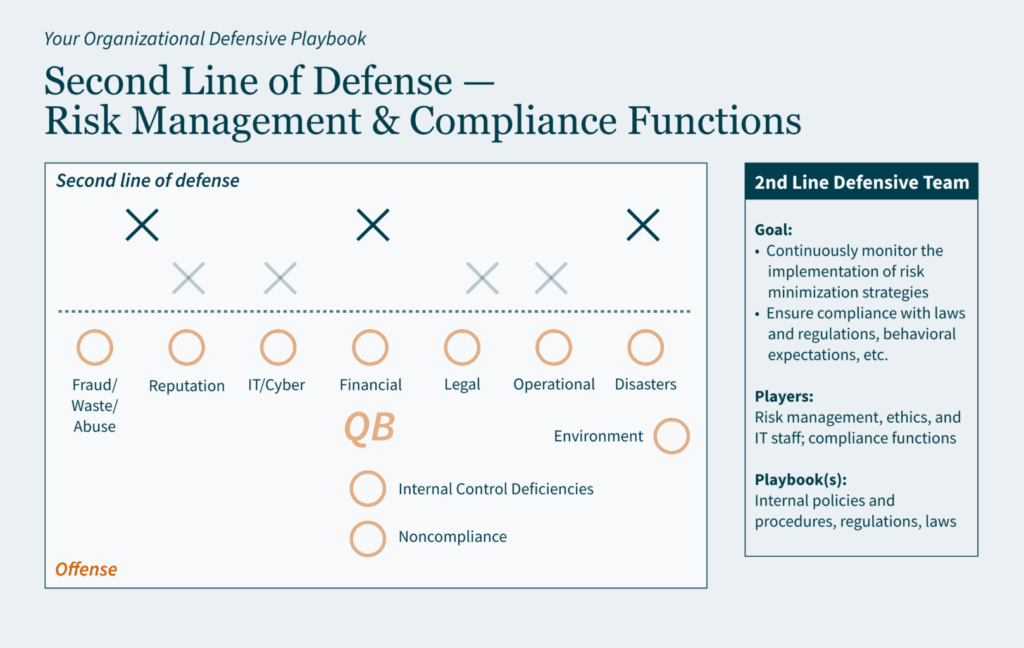
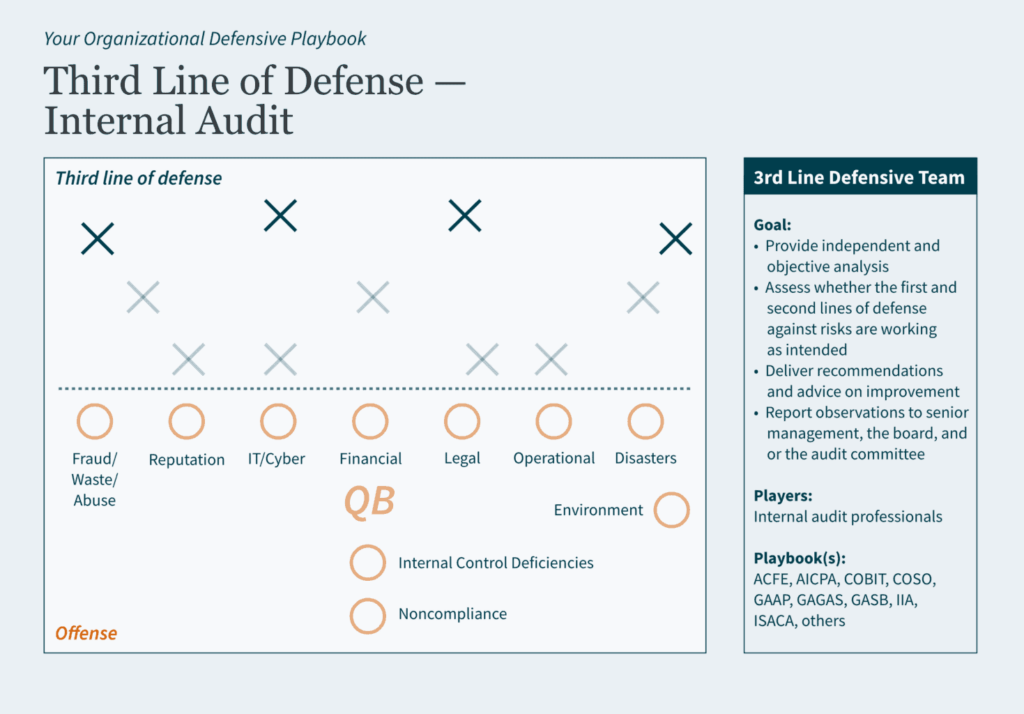
Key Takeaways:
- The intoxicating hemp industry offers exciting opportunities for innovation and revenue growth, but navigating its complex and changing regulatory landscape requires adaptability and strategic planning.
- While consumer demand for intoxicating hemp products is surging, businesses face challenges like a changing regulatory environment, banking hurdles, and the need for extensive consumer education.
- Success in this evolving market demands a comprehensive strategy addressing compliance, financial management, and risk mitigation to capitalize on opportunities while navigating regulatory changes.
- Whether you agree with how these products came to market, many now believe that they will survive the regulatory process in some form, most likely in an environment with state-by-state regulations.
~
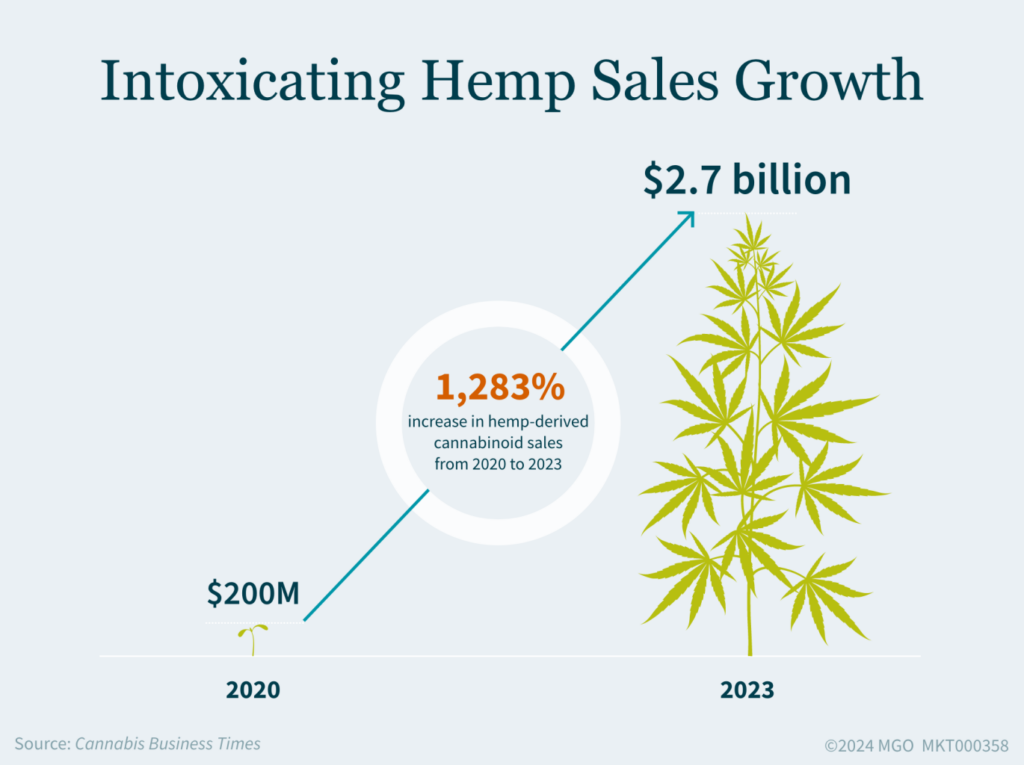
Intoxicating hemp products have had explosive growth but are now facing regulatory and other headwinds, with states like California, Missouri, and New Jersey introducing new regulations to control their sale and distribution. For intoxicating hemp companies, or those considering entering this space, you are navigating a complex landscape that offers both significant opportunities and substantial challenges. In this evolving industry, it is essential to understand the market dynamics, regulatory environment, and how to manage your business effectively.
The Rise of Intoxicating Hemp
Intoxicating hemp products are the result of wording in the 2018 Farm Bill, which created a gray area where alternative cannabinoids — such as Delta-8 THC, Delta-10 THC, HHC, and a host of other compounds — have come into existence.
Since then, due to the ability to access traditional retail channels (including direct-to-consumer) and a lower tax and regulatory burden compared to cannabis, the market for intoxicating hemp products has exploded. These products, which offer consumers a legal alternative to traditional cannabis, have gained popularity in the form of beverage, tinctures, vapes, and other consumables. While this boom presents exciting opportunities, it also introduces a host of challenges for those entering or already operating in the intoxicating hemp industry.
Opportunities in the Intoxicating Hemp Market
The intoxicating hemp industry offers several key opportunities for companies looking to expand or diversify their product lines:
1. Rising Consumer Demand
The demand for intoxicating hemp products has skyrocketed. Products such as Delta-8 THC and Delta-9 THC are increasingly popular due to their similar effects to cannabis while staying within a legal gray area and being more widely available. Gummies and beverages, in particular, have emerged as popular product forms — with beverages providing an appealing alternative as younger generations report decreased alcohol consumption. This creates a growing market for your business to tap into.
Curaleaf, Kiva, Medterra, Wyld, 1906, and Tilray — which just recently launched a lineup of hemp-derived Delta-9 THC mocktails, seltzers, and sparkling drinks in the U.S. — are among the cannabis companies that have already entered the hemp market. In a recent Cannabis Business Times survey, 17% of participants from state-legal cannabis businesses said they are currently growing or selling intoxicating hemp-derived cannabinoid products and 26% said they are considering or would consider growing or selling intoxicating hemp products.
2. New Revenue Streams
For cannabis operators and hemp sellers, the intoxicating hemp market offers a way to diversify revenue streams. If you are already in the cannabis business, adding hemp-derived products can provide a complementary line that broadens your market reach. While regulations continue to evolve, potential remains to sell in more mainstream retail spaces — further increasing revenue opportunities.
3. National Scaling and Partnerships
One of the key advantages of intoxicating hemp is the ability to scale your brand nationally through interstate commerce. Unlike cannabis, which faces strict state-by-state regulations, intoxicating hemp can be legally shipped across state lines. Additionally, forming strategic partnerships with other brands, such as those in the food and beverage industry, can further enhance your product offerings and brand visibility.
Challenges Facing Intoxicating Hemp Companies
Despite the many opportunities, the intoxicating hemp industry is not without its challenges — including:
1. Regulatory Uncertainty
Perhaps the most significant challenge facing intoxicating hemp businesses is regulatory uncertainty. While the update to the 2018 Farm Bill appears to be deferred, many states have moved to restrict intoxicating hemp derivatives like Delta-8.
For example, New Jersey recently mandated that intoxicating hemp goods fall under the same regulatory system as cannabis. California has implemented emergency regulations, while Missouri’s governor ordered the removal of intoxicating hemp products from the market. Other states, like Louisiana and Connecticut, are implementing new restrictions without outright bans.
This regulatory landscape is likely to continue evolving, with the possibility of stricter federal oversight in the future. Your business model and product offerings need to be flexible enough to adapt to these changes — and the potential uncertainty ahead.
2. Market Saturation and Consumer Confusion
The initial boom in Delta-8 and other intoxicating hemp products has led to market saturation in some regions, increasing competition and potentially driving down profit margins. Adding to this challenge is consumer confusion. Many customers still struggle to differentiate between hemp, cannabis, CBD, and various THC isomers. As a result, educating consumers about products is crucial to building trust and expanding your customer base.
3. Financial Hurdles
While intoxicating hemp companies generally face fewer banking restrictions than cannabis companies, many financial institutions remain hesitant to work with businesses in this space. This can make basic operations challenging — from processing payments to securing loans. You may need to work with specialized financial service providers or explore alternative banking solutions. It is also crucial to maintain meticulous financial records and be prepared for extra scrutiny from financial institutions.
Navigating the Industry’s Complexities
While the intoxicating hemp market offers exciting opportunities for growth and innovation, it also comes with its fair share of challenges. To succeed in this evolving industry, it is crucial to have a comprehensive strategy that addresses compliance, financial management, and risk mitigation. With the right support, you can navigate these complexities and position your business for growth in this fast-growing market.
How We Can Help
Our dedicated Cannabis team understands the unique challenges you face in the intoxicating hemp landscape. We offer a range of services to help guide your efforts — from inventory accounting to tax strategy to help obtaining banking services. Reach out to our team today to learn how we can help you thrive in the intoxicating hemp market.