Key Takeaways:
- Proactive planning means focusing on the “how” instead of just the “what” — turning basic questions into actionable strategies for effective implementation.
- An ecosystem perspective involves considering the broader impact on third-party stakeholders to ensure the entire supply chain is prepared for going public.
- Holistic risk management requires cross-functional collaboration to coordinate risk mitigation, enhancing organizational resilience against new public company risks.
~
Preparing for your initial public offering (IPO) means investigating every facet of the business — not only to obtain the best possible valuation, but also to make the changes necessary to operate as a public company and achieve long-term growth. Asking the right questions can help you see beyond the obvious, illuminating factors you may have otherwise overlooked and setting your organization up for post-IPO success.
Here are five ways to take common IPO questions from a basic 101 level up to a more advanced 201 to deepen readiness and unlock new value.
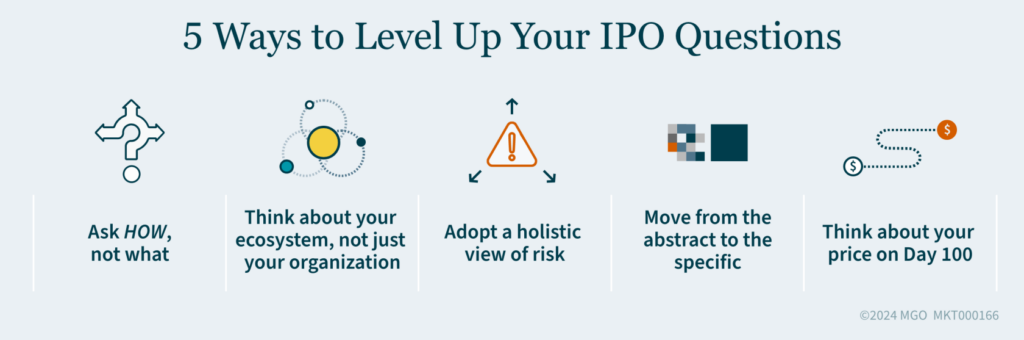
IPO Checklist: 5 Ways to Level Up Your IPO Questions
1. Ask “How”, Not “What

Don’t plan passively. Approach key questions in a way that mandates proactive action rather than reactive changes. A seemingly small alteration — a “how” instead of a “what” — can transform a basic inquiry into a forcing function that spurs teams to take concrete steps.
- 101: What new reporting obligations will we face as a public company?
- 201: How can we resource and connect our finance, IT, and legal teams to meet new reporting requirements on time and without misstatements?
While the 101 question can establish new reporting needs and responsibilities, the 201 question goes further, pushing leaders to actively plan toward these goals.
2. Think About Your Ecosystem, Not Just Your Organization

Going public brings scrutiny from new stakeholders, such as boards, shareholders, and regulators. It is no longer enough for leaders to focus on their organization alone. Instead, they must broaden their perspective to consider the effects of all changes — new regulations, reporting requirements, cybersecurity risks, and more — on their third-party ecosystem.
- 101: What new laws and regulatory bodies apply to our business as a public company?
- 201: Are we prepared to validate that our third-party providers, in addition to our own organization, are complying with any new requirements?
Answering the 201 question requires looking beyond the organization to consider the risks posed by third-party partners. Financial institutions, for example, will need to verify that any third-party service providers comply with existing consumer protection laws under Dodd-Frank.
Cutting across all industries, the Securities and Exchange Commission (SEC) adopted new rules in 2023 requiring public companies to disclose any material cybersecurity intrusions or breaches, as well as information about their cyber risk management, governance, and security. Companies pursuing an IPO must prepare to comply with these new requirements themselves and be ready to validate that any third-party providers can also remain compliant.
3. Adopt a Holistic View of Risk

Effective risk management requires cross-functional cooperation and communication. No matter the business area — cybersecurity, operations, supply-chain management — identifying risks is not enough; nor is simply naming the strategies to mitigate risks.
- 101: What new risks are most relevant to our business as we prepare for operations as a public company?
- 201: What is each department’s risk mitigation responsibility, and where are there opportunities for coordination?
Every department has a role to play in risk mitigation. Clearly defining those roles and the interconnections between them can build resilience in the lead up to an IPO and help companies adapt to new risks after going public.
4. Move from the Abstract to the Specific

Tailoring approaches to specific objectives will help you manage more variables and define what kind of public company you want to be. Whenever possible, leaders should design questions to address specific challenges, rather than using general terms.
- 101: Who are the new stakeholder audiences (e.g., board members and regulators) with whom we need to establish communications as a public company?
- 201: How will we communicate with board members, shareholders, and regulators? What tools, channels, and reporting structures will we build?
The 101 question identifies an important consideration, but it stops there. The 201 question addresses finding and filling in the gaps. You can use what you know to pave the way toward learning what you don’t.
5. Think About Your Price on Day 100
The IPO is not an end-state; it is the beginning of a new chapter. Every action taken in service of a public offering must also include a path to further growth.
- 101: How do we obtain the best possible valuation for our company?
- 201: How can we leverage our momentum to improve our valuation 100 days after going public?
The 101 question speaks to an important need, but its focus is limited. Success as a public company demands growth beyond the IPO event. Asking the 201 question can help you embed a future-focused mindset into all planning decisions. The day one valuation matters, but so does valuation on day 100 — and beyond.
How MGO Can Help
Navigating the complexities of an IPO requires guidance and a comprehensive strategy. MGO’s Transaction Advisory Services team supports you throughout the process, from proactive planning to risk management, so that your entire ecosystem is ready for the transition. Reach out to our team today to discover how MGO can help you achieve your long-term growth objectives and post-IPO success.