Key Takeaways:
- IT assessments find vulnerabilities and threats, enabling organizations to implement proactive measures and strengthen their security posture.
- Regular IT assessments help organizations adhere to industry standards and regulatory requirements, avoiding legal penalties and maintaining customer trust.
- By safeguarding IT systems and confirming their integrity and availability, IT assessments play a crucial role in business continuity and resilience against disruptions.
~
In today’s rapidly evolving digital landscape, keeping robust and secure information technology (IT) systems is paramount for the success and sustainability of any organization. IT assessments have emerged as a vital part of an effective IT advisory strategy, providing your organization with a comprehensive understanding of its IT infrastructure, finding vulnerabilities, and helping you align with industry standards and regulatory requirements.
IT assessments involve a thorough evaluation of your organization’s IT environment — encompassing systems, networks, applications, and data assets. These assessments aim to show weaknesses, verify compliance, and offer actionable insights to enhance your overall IT performance and security. The scope of IT assessments includes various elements such as risk assessment, IT security management, policy reviews, access controls, network security, data protection, and incident response preparedness.
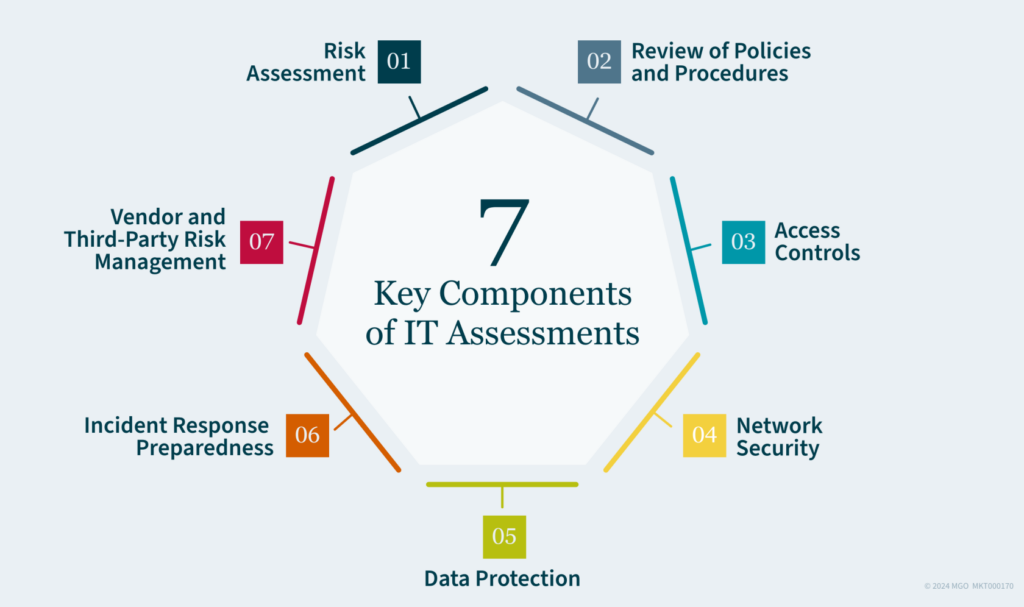
Key Components of IT Assessments
IT assessments typically encompass the following key components, each critical for a comprehensive evaluation of your organization’s IT infrastructure:
- Risk assessment: Conducting a risk assessment is foundational to understanding potential threats and vulnerabilities within your organization’s IT environment. This involves evaluating factors such as cybersecurity threats, data breaches, insider threats, and regulatory non-compliance. Identifying and prioritizing risks based on their potential impact allows your organization to implement proactive measures to mitigate these risks.
- Review of policies and procedures: Policies and procedures form the backbone of your organization’s IT framework. Evaluating these policies confirms they are comprehensive, up-to-date, and aligned with industry standards and regulatory requirements. Effective policies facilitate enforcement and adherence, significantly reducing the risk of IT-related incidents.
- Access controls: Implementing robust access controls is crucial for protecting sensitive data and systems. Assessing access controls involves evaluating user access rights, privileges, and authentication mechanisms. Effective access controls prevent unauthorized access and mitigate the risk of data breaches.
- Network security: Your organization’s network architecture, configuration, and security controls must be assessed to identify vulnerabilities and potential points of compromise. This includes reviewing firewalls, intrusion detection and prevention systems (IDPS), virtual private networks (VPNs), and network segmentation practices.
- Data protection: Data protection measures such as encryption, data loss prevention (DLP) controls, and data backup and recovery procedures are vital for safeguarding sensitive information. Confirming these measures helps protect your data against unauthorized access, disclosure, or alteration.
- Incident response preparedness: Effectively responding to IT incidents is critical to minimize damage and recovery time. Reviewing incident response plans and procedures — including incident detection, reporting mechanisms, and escalation processes — confirms your organization is prepared to handle IT incidents efficiently.
- Vendor and third-party risk management: Many organizations rely on third-party vendors and service providers, introducing additional IT risks. Assessing your organization’s practices for managing these risks, including vendor contracts and due diligence processes, is essential for mitigating supply chain vulnerabilities.
Why IT Assessments Are Essential for Your Organization
IT assessments are not just a regulatory requirement; they are a strategic necessity. IT assessments offer several key benefits for your organization, including:
- Find potential vulnerabilities and threats before they are exploited, allowing your organization to implement proactive measures to mitigate risks.
- Verify compliance with industry standards and regulatory requirements to help you avoid legal penalties and keep customer trust.
- Strengthen your organization’s overall security posture to reduce the likelihood of successful cyberattacks.
- Offer the insights you need for effective risk management, enabling the allocation of resources to address the most critical threats.
- Safeguard your business continuity by confirming the integrity and availability of IT systems, protecting your organization against disruptions caused by IT incidents.

The Critical Importance of IT Assessments for Modern Enterprises
In an era where IT systems are the backbone of business operations, the importance of IT assessments cannot be overstated. These assessments provide your organization with a clear understanding of its IT vulnerabilities and offer you a roadmap for mitigating risks.
By investing in regular IT assessments, you will not only help protect your digital assets but also support business continuity and keep stakeholder trust. For enterprises striving to stay ahead in the digital age, IT assessments are an indispensable part of a robust IT advisory strategy.
To learn how MGO’s IT Advisory Solutions can fortify your organization’s defenses, reach out to our team today.