Key Takeaways:
- Implementing public-company-level internal controls early on can help your private company prepare for a potential IPO or acquisition, ultimately reducing the risk of adverse disclosures and easing your transition.
- Private companies experiencing fast growth can benefit from stronger controls to prevent fraud and other errors, so that financial data remains reliable no matter how big they scale.
- If you enhance your internal controls, you can increase your credibility with investors, banks, and other stakeholders — potentially lowering costs and adding financial security.
- If you are in an industry with public peers or high security standards (like utilities or tech), you might benefit from adopting similar control measures to maintain competitiveness and stakeholder confidence.
~
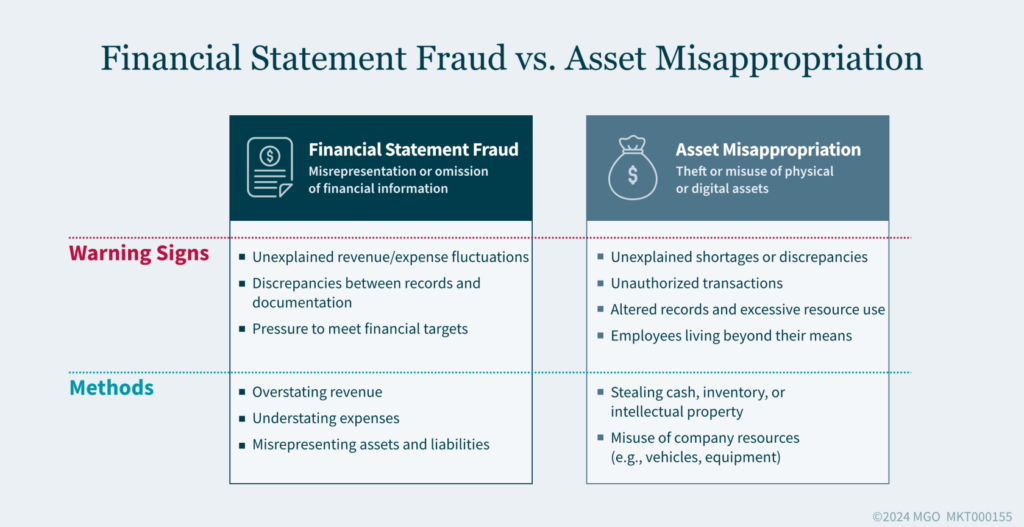
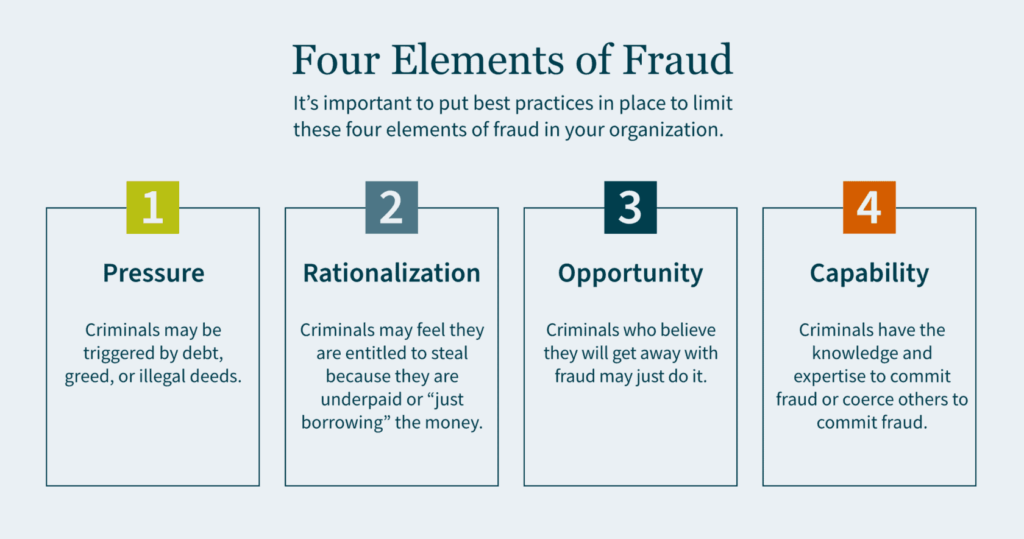
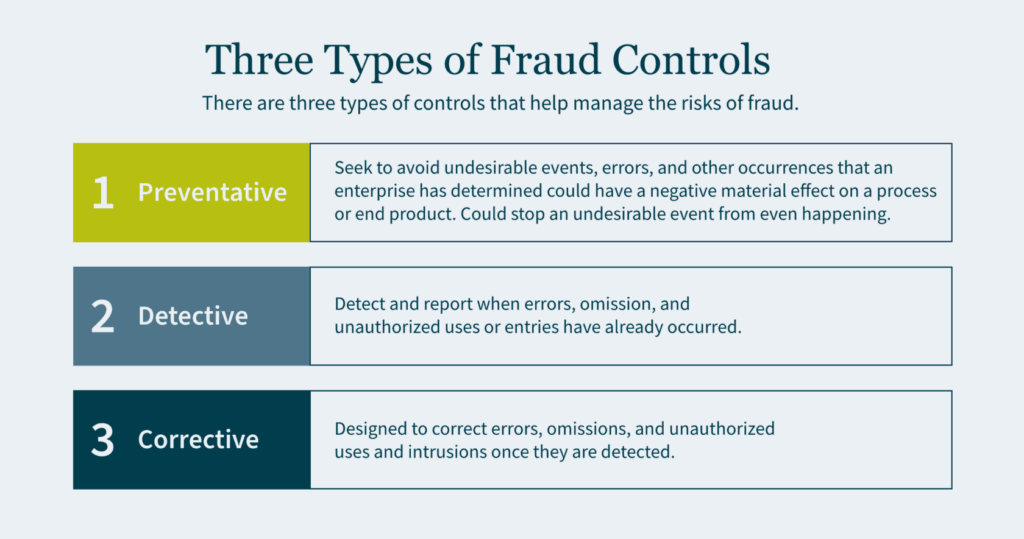
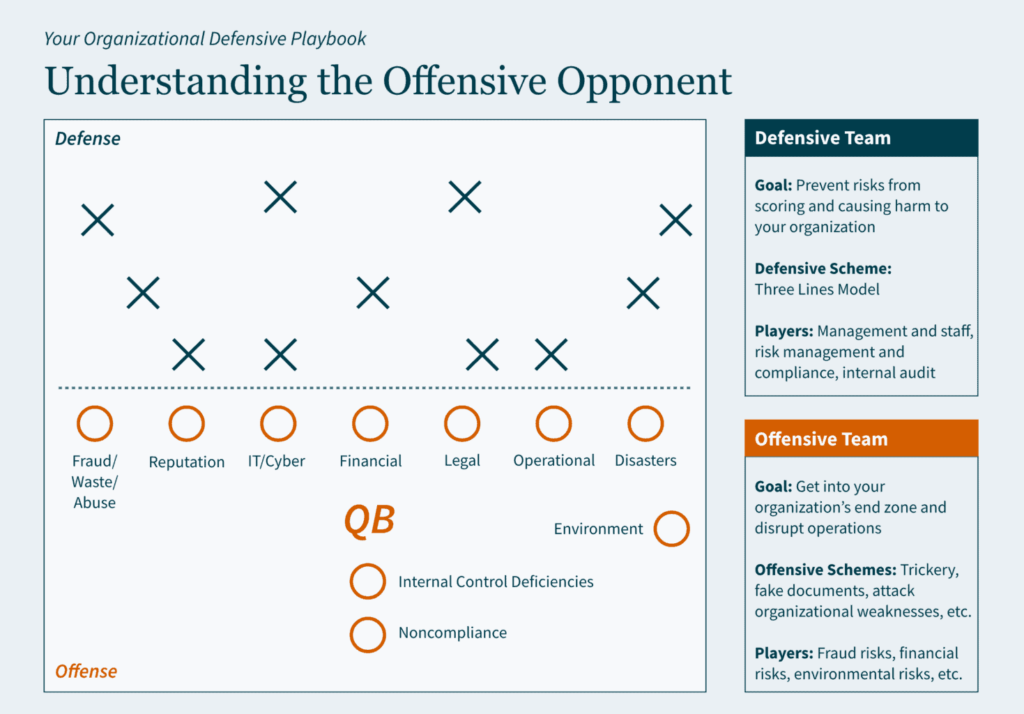
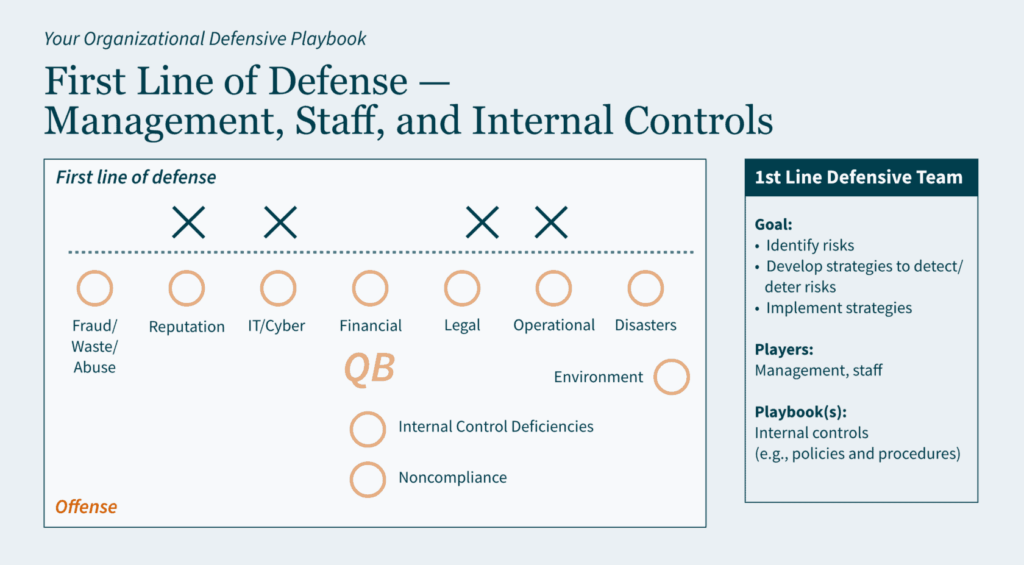
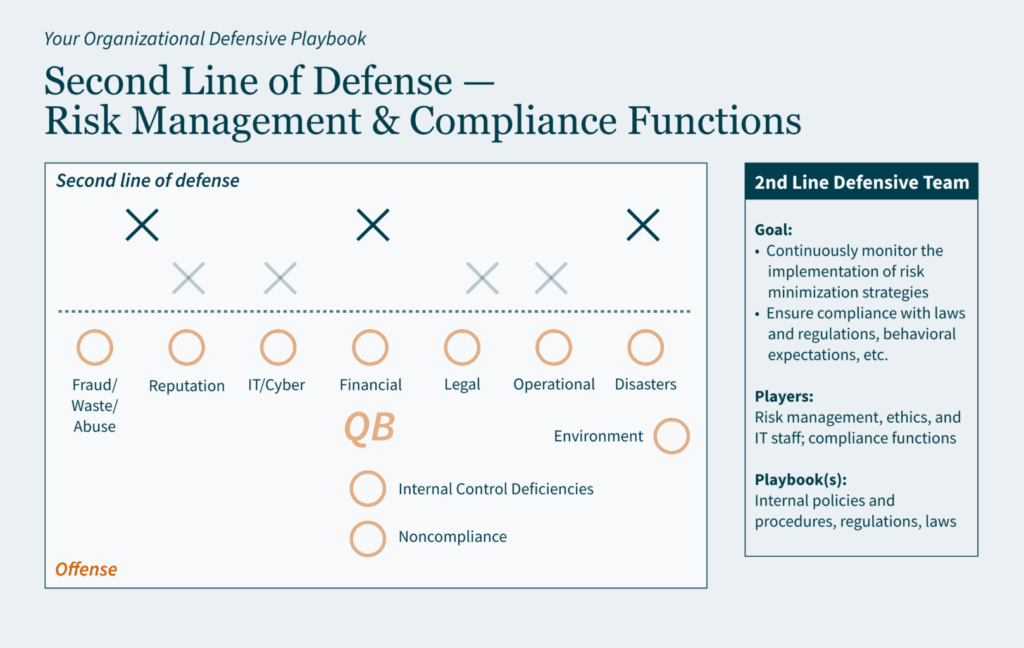
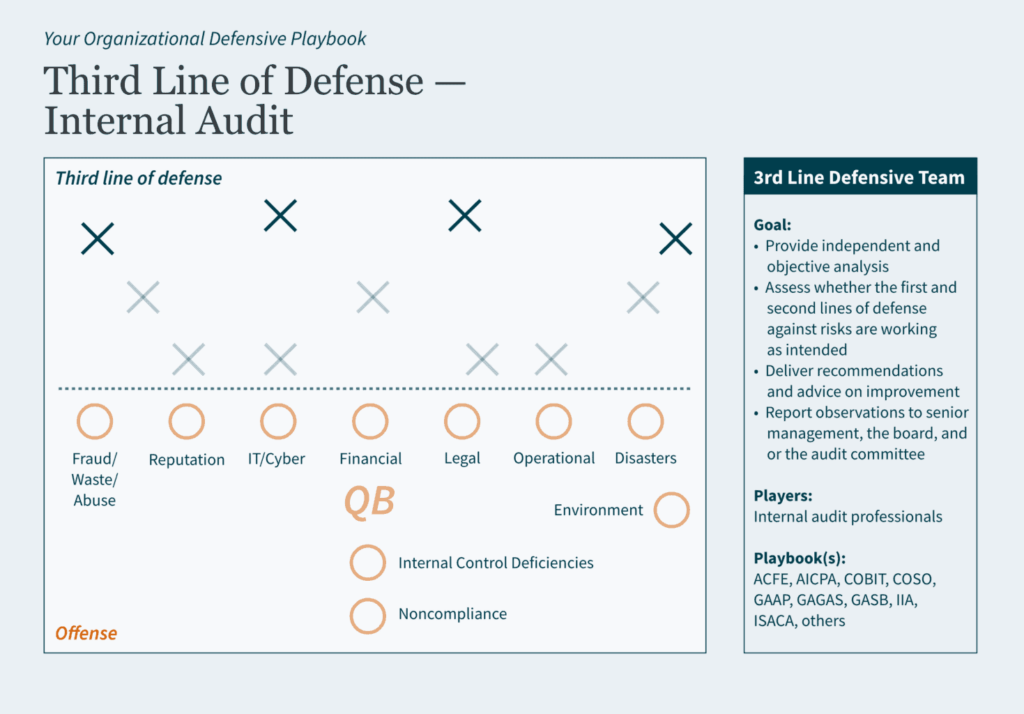
Often viewed as a “public company problem,” private organizations may want to consider implementing internal controls similar to Sarbanes-Oxley (SOX) Section 404 requirements. The inherent benefits of a strong control environment may be significant to a private company; they enhance accountability throughout the organization, reduce risk of fraud, improve processes and financial reporting, and provide more effective engagement with the board of directors.
While not always smaller, private organizations often have limited resources in specialty areas, including accounting for income tax. This resource constraint — with the work being performed outside the core accounting team — combined with the complexity of the issues means private companies are ideal candidates for, and can achieve significant benefit from, internal controls enhancements.
Thinking ahead, there are five reasons private companies may want to adopt public-company-level controls:
- Initial Public Offering (IPO) — Walk before you run! If the company believes an IPO may be in its future, it’s better to “practice” before the company is required to be SOX compliant. A phased approach to implementation can drive important changes in company culture as it prepares to become a public organization. Recently published reports analyzing IPO activity and first-time internal control over financial reporting (ICFR) assessments reveal that adverse disclosures on internal controls are three times more likely to be made during a first-time assessment. Making a rapid change to SOX compliance without proper planning can place a heavy burden on a newly public company.
- Private Equity (PE) Buyer — If it is possible that the company will be sold to a PE buyer, enhanced financial reporting controls can provide the potential buyer with an added layer of security or confidence regarding the company’s financial position. Further, if the PE firm has an exit strategy that involves an IPO, the requirement for strong internal controls may be on the horizon.
- Rapid Growth — Private companies that are growing rapidly, either organically or through acquisition, are susceptible to errors and fraud. The sophistication of these organizations often outpaces the skills and capacity of their support functions, including accounting, finance, and tax. Standard processes with preventive and detective controls can mitigate the risk that comes with rapid growth.
- Assurance for Private Investors and Banks — Many users other than public shareholders may rely on financial information. The added security and accountability of having controls in place is a benefit to these users because the enhanced credibility may affect the organization’s cost of borrowing.
- Peer-Focused Industries — While not all industries are peer-focused, some place significant weight on the leading practices of their peers. Further, some industries require enhanced levels of security and control. For example, utility companies, industries with sensitive customer data (financial or medical), and tech companies that handle customer data often look to their peer groups for leading practices, including their control environment. When the peer group is a mix of public and private companies, a private company can benefit from keeping pace with the leading practices of their public peers.
Private companies are not immune from intense stakeholder scrutiny into accountability and risk. Companies with a clear understanding of the inherent risks that come from negligible accounting practices demonstrate the ability to think beyond the present and to be better prepared for future growth or change in ownership.
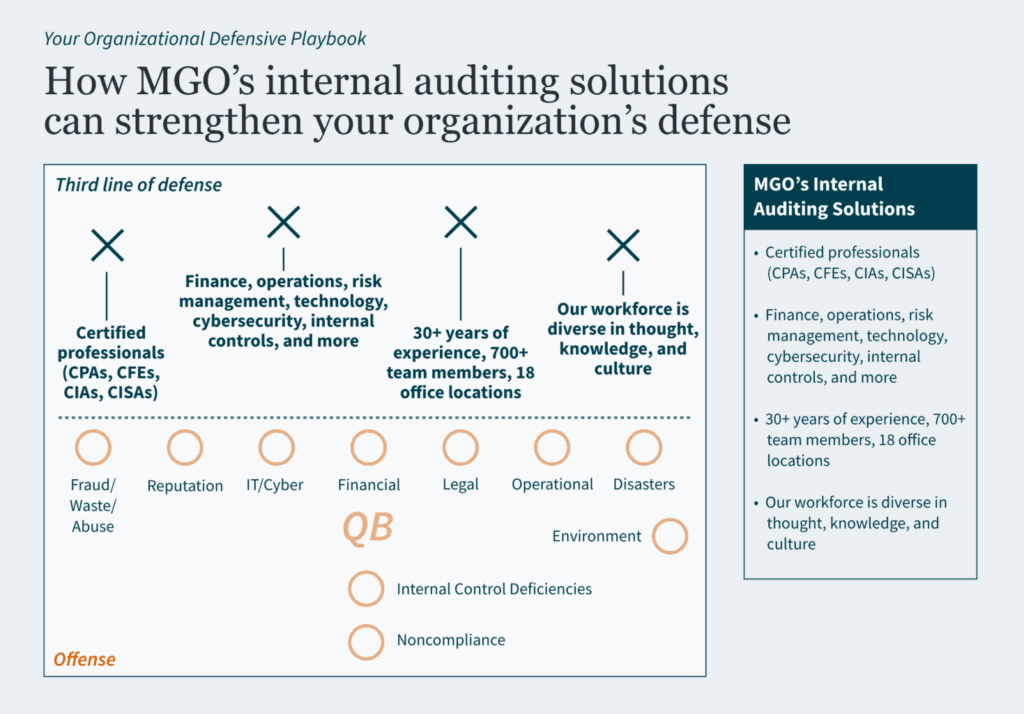
How MGO Can Help
We offer a comprehensive approach to internal control implementation, personalized to meet your private company’s unique needs. Our team’s experience in audit, risk management, and advisory can help your business establish robust controls that enhance accountability, reduce fraud risk, and prepare for the future — whether that looks like growth or a public offering.
Whether you are preparing for an IPO, meeting private equity expectations, or merely enhancing your operational efficiency, our team provides the guidance and the tools needed to help you navigate any complexity with confidence. To learn more about how we can assist your business, reach out to us today.