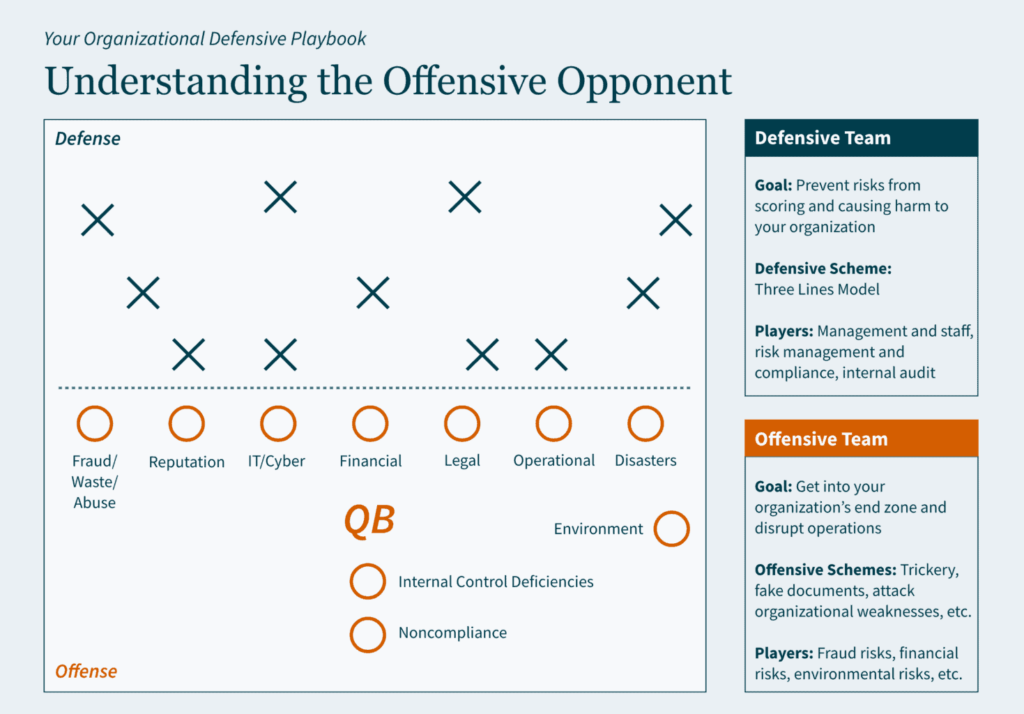
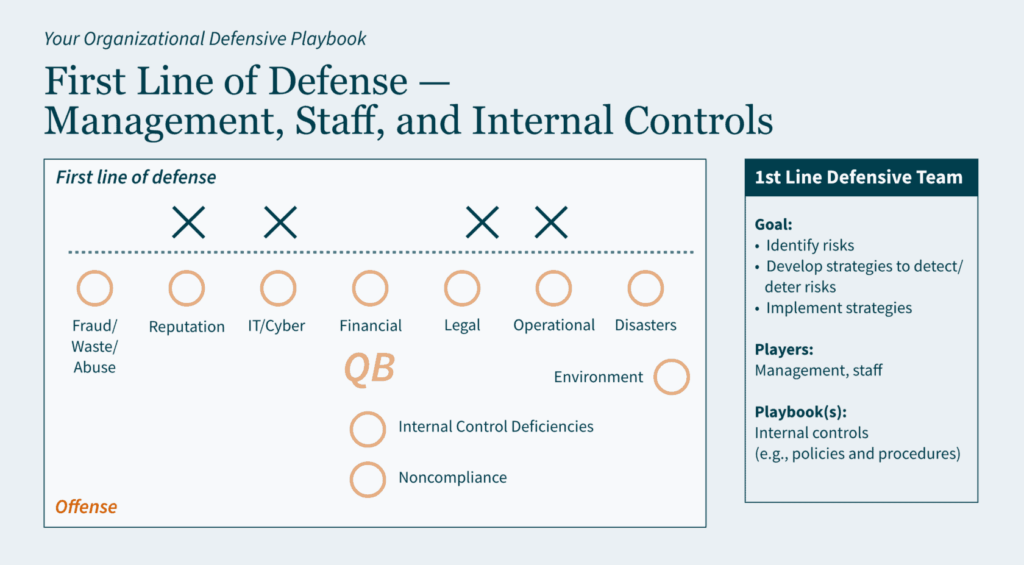
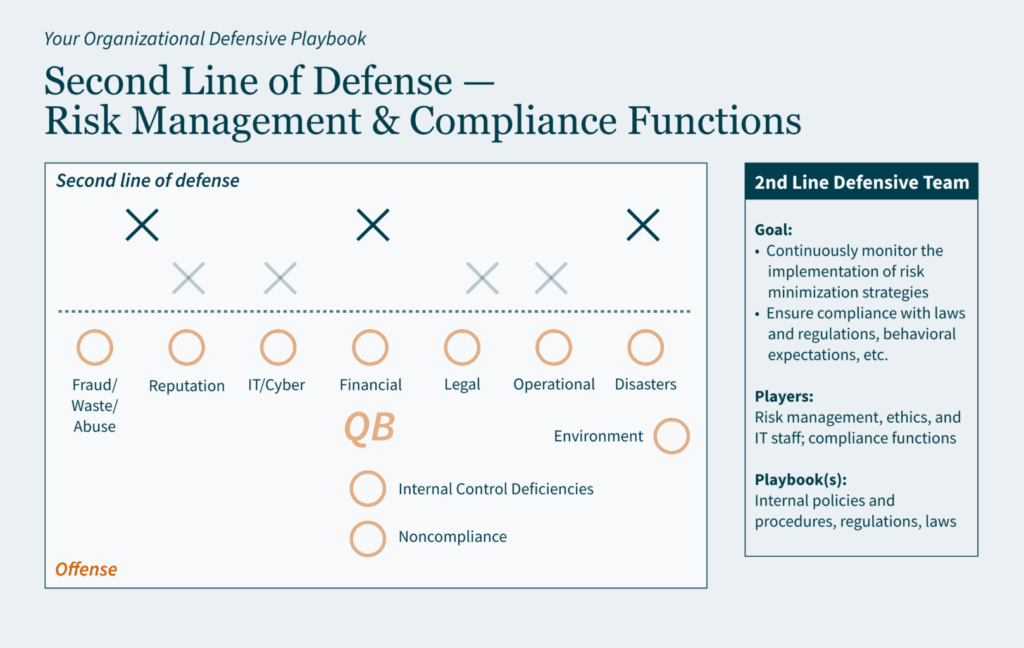
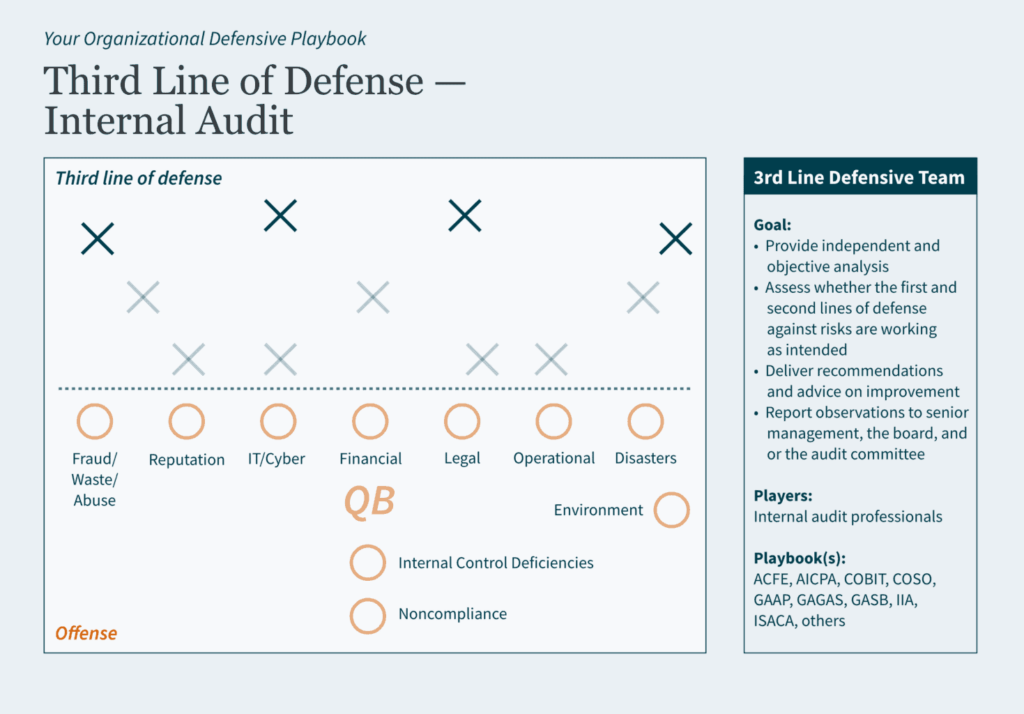
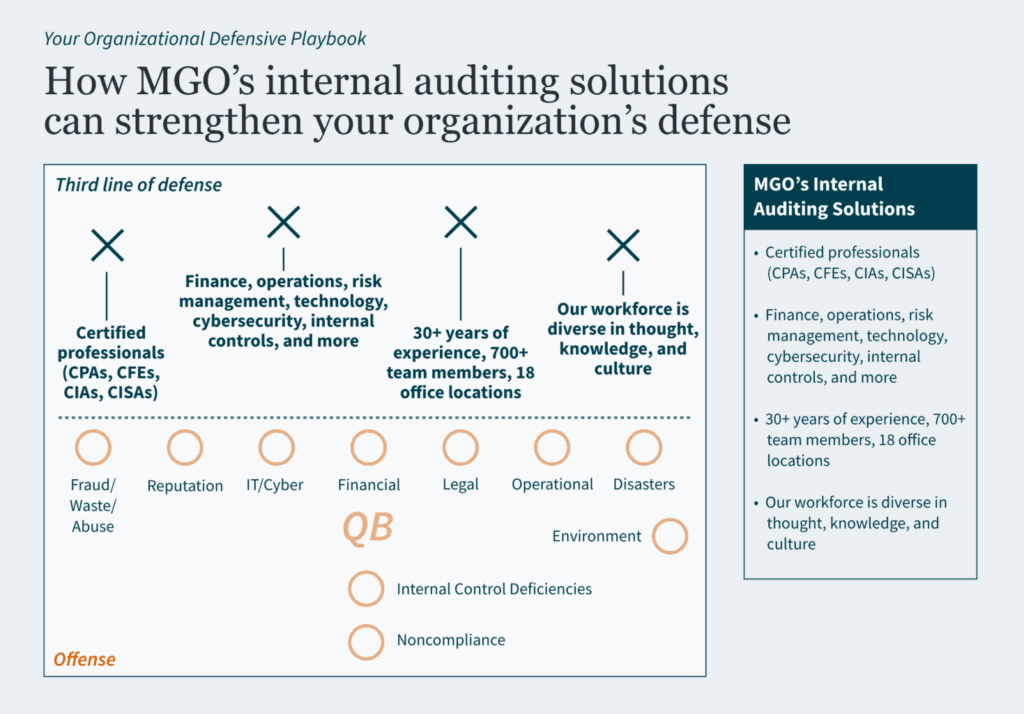
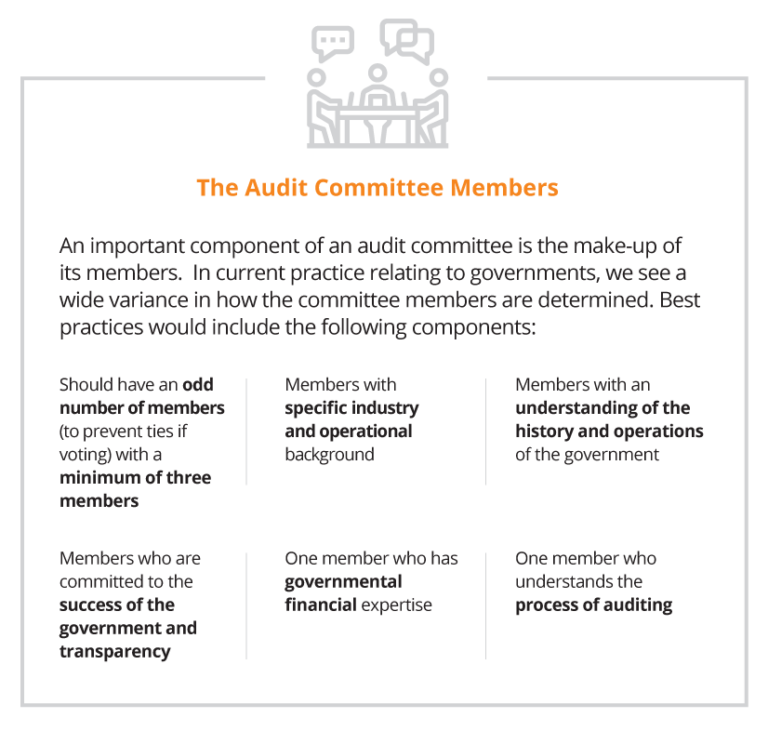
Key Takeaways:
- Asset misappropriation involves the theft or misuse of an organization’s physical and digital assets, posing a major threat to businesses.
- Red flags of asset misappropriation include unexplained shortages, unauthorized transactions, altered records, excessive resource use, and employees living beyond their means.
- Strategies to combat asset misappropriation include strong internal controls, employee education, surveillance technology, promoting an ethical culture, and data analytics for fraud detection.
~
In the dynamic landscape of modern business, asset misappropriation remains a pervasive threat, undermining the financial stability and integrity of organizations across industries. As part of MGO’s fraud series, this article delves into the critical issue of asset misappropriation — offering your business the knowledge and tools needed to safeguard your valuable assets.
Understanding Asset Misappropriation
Asset misappropriation, a prevalent form of fraud, involves the theft or misuse of an organization’s assets. Unlike financial statement fraud, which distorts the truth on paper, asset misappropriation manifests in the direct pilfering or misuse of physical and digital assets. From cash and inventory to intellectual property and digital data, no resource is immune to this fraudulent activity.
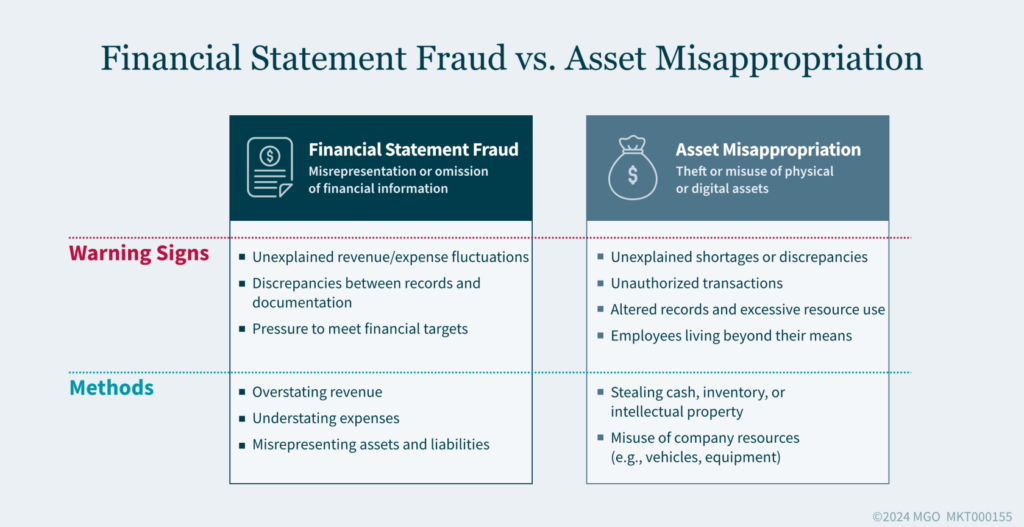
Red Flags of Asset Misappropriation
- Unexplained shortages or discrepancies: Whether it is cash, inventory, or other assets, unexplained shortages are classic signs of theft or embezzlement. For instance, casinos might notice discrepancies in chips or cash, pointing toward internal theft.
- Unauthorized transactions: Any unauthorized withdrawals or transfers, especially in sensitive environments like casino accounts or gaming tables, should raise immediate concerns about asset misappropriation.
- Alteration of records: Manipulating gaming records, player accounts, or payout systems can facilitate theft, often going unnoticed without rigorous audits.
- Excessive use of company resources: When employees use company vehicles, equipment, or facilities beyond their professional needs, it suggests potential misuse of organizational assets for personal gain.
- Lifestyle inconsistencies: Employees exhibiting a lifestyle significantly above their income level can be a red flag for embezzlement or fraud, often funded by stolen assets.
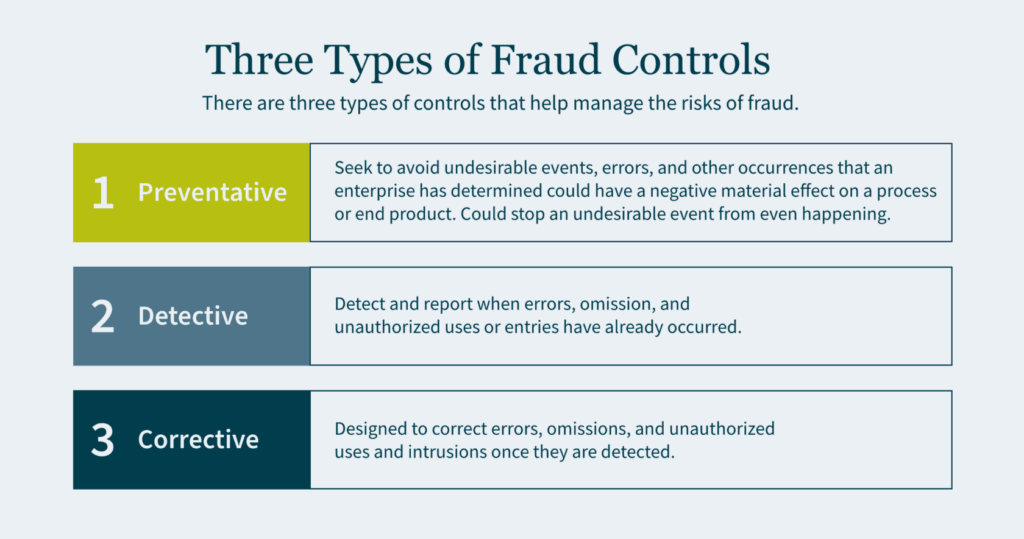
Strategies to Combat Asset Misappropriation
To effectively shield your organization from the perils of asset misappropriation, a multifaceted approach is necessary. These strategies are designed to fortify your defenses, helping your business operate with the highest standards of integrity and security. By implementing these measures, you can create a resilient barrier against fraudulent activities and safeguard your organization’s future.
Here are some pivotal strategies to combat asset misappropriation:
- Establishing robust internal controls is the first line of defense. Professionals with experience enhancing internal controls can assist your organization in assessing and refining its practices — including segregation of duties, regular audits, and securing access to sensitive areas and systems. This approach establishes a solid foundation for preventing asset misappropriation.
- Educating employees about the signs of fraud and the importance of ethical behavior is essential to deter potential fraudsters and empower your staff to report suspicious activities. Training programs, which can be supported by advisory firms, effectively communicate the risks of fraud and the importance of vigilance, helping to build a knowledgeable and proactive workforce.
- Utilizing technology like surveillance cameras, advanced access controls, and cybersecurity measures can significantly reduce the risk of asset theft or misuse. Cybersecurity and physical security professionals can integrate cutting-edge solutions to protect your assets from both internal and external threats, providing a comprehensive defense strategy.
- Promoting a corporate culture that values honesty and transparency can discourage fraudulent behavior. Developing policies and practices that foster open communication and a strong ethical foundation is crucial. Establishing a whistleblowing policy that encourages reporting without fear of retaliation can be an integral part of this effort.
- Deploying data analytics and fraud detection software to monitor for unusual patterns or anomalies can indicate asset misappropriation. Advanced data analytics and forensic accounting services can identify and investigate suspicious activity, using sophisticated tools to detect early signs of fraud and prevent asset loss.

Safeguarding Your Assets Against Pervasive Threats
Asset misappropriation poses a significant risk to businesses, draining resources and eroding stakeholder trust. By understanding the red flags and implementing a comprehensive strategy to detect and prevent asset misappropriation, your organization can protect its assets and maintain its financial integrity.
MGO’s Business Advisory solutions offer a pathway to strengthen your defenses against the risks of asset misappropriation. For a deeper dive into how we can help protect your business, reach out to our team today.
This article is part of our ongoing fraud series, “Alert Signals: Uncovering the Spectrum of Fraud,” aimed at educating your business on identifying and preventing fraudulent activities. Read the previous article in the series on spotting red flags of financial reporting fraud and stay tuned for more insights and strategies to protect your organization.