Executive Summary:
- Internal controls, especially around fraud prevention, are essential for limiting losses, driving efficiency, improving accountability, and boosting company value during investments or M&A deals.
- The “tone at the top” from leadership in fostering an ethical environment, along with proper segregation of duties, are key elements for fraud prevention and strong internal controls.
- Well-established policies and procedures, like Delegation of Authority rules and restricted system access protocols, are also vital for maintaining adequate controls to enable company growth.
~
As the economy stands on shaky legs, private equity and venture capital firms are necessarily careful and strategic when assessing potential investment opportunities. Whether your long-term plan includes acquiring another company, selling your business, or seeking new capital, strengthening your internal control environment — with a focus on preventing fraud — is a powerful way to increase actual and perceived value.
In the following, we will lay out the reasons why fraud prevention is an essential element to proper corporate governance and illustrate key areas to examine whether your internal control environment is built to help your operation succeed.
The Importance of Internal Controls in Fraud Prevention
A robust internal control system is the first step toward managing, mitigating, and uncovering fraud. A strong internal control environment will:
Protect your company’s assets by reducing the risk of theft or misappropriation of cash, inventory, equipment, and intellectual property.
Detect fraudulent activities or irregularities early on and deter employees from attempting fraud in the first place.
Provide cost savings by limiting opportunities for financial losses, costly investigations, and legal expenses associated with fraud.
Drive operational efficiency by providing clear processes and guidelines that reduce the risk of errors or inefficiencies in day-to-day operations.
Improve employee accountability by implementing checks and balances that discourage unethical behavior.
When seeking an investment or undertaking a significant M&A deal, you should have a firm grasp of the strength and quality of your internal control environment. Not only will you reduce the risk of fraud in the near term, but you will also cultivate confidence with potential investors and M&A partners.
Fraud Prevention Starts with the “Tone at the Top”
The first key element to look for in measuring the strength of your internal controls is ensuring a clear and proactive “tone at the top”, meaning an ethical environment fostered by the board of directors, audit committee, and senior management. A good tone at the top encourages positive behavior and helps prevent fraud and other unethical practices.
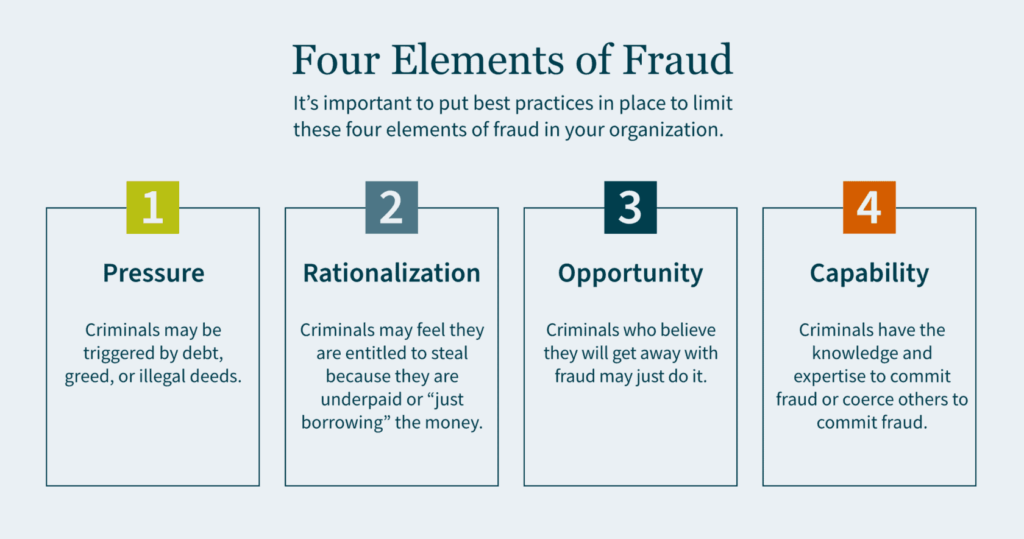
There are four elements to fraud: pressure, rationalization, opportunity and capability.
Pressure motivates crime. This could be triggered by debt, greed, or illegal deeds. Individuals who have financial problems and commit financial crimes tend to rationalize their actions. Criminals may feel that they are entitled to the money they are stealing, because they believe they are underpaid. In some cases, they simply rationalize to themselves that they are only “borrowing” the money and have every intention of paying it back.
Criminals who can commit fraud and believe they will get away with it may just do it. Capability means the criminal has the expertise as well as the intelligence to coerce others into committing fraud. The board of directors is responsible for selecting and monitoring executive management to ensure best practices are in place to limit the motivations of all four elements of fraud.
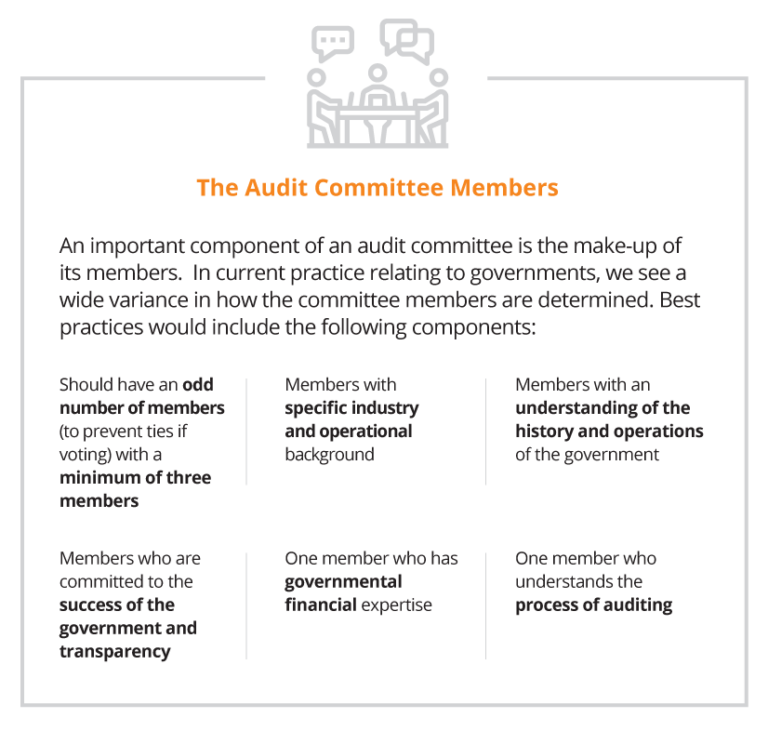
Proper Segregation of Duties for Internal Controls
The second key element to look for in your internal controls is a well-established segregation of duties. The idea is to establish controls so that no single person has the ability that would allow them the opportunity to commit fraud. Companies must make it extremely difficult for any single employee to have the opportunity to perpetrate a crime and subsequently cover it up.
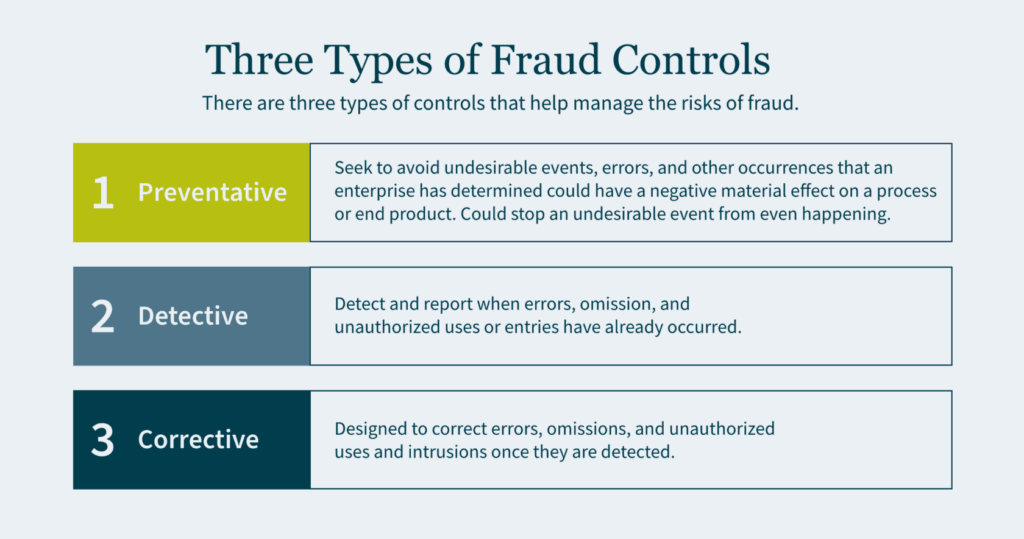
Fraud Controls
There are three types of controls that help manage the risks of fraud: preventative, detective, and corrective.
- Preventative controls seek to avoid undesirable events, errors, and other occurrences that an enterprise has determined could have a negative material effect on a process or end product. Preventative controls are the best of the three as they are the first line of defense and a backstop to fraud. If designed correctly, preventative controls stop an undesirable event from even happening.
- Detective controls exist to detect and report when errors, omission, and unauthorized uses or entries have already occurred. Although it is important to identify these adverse events, you are doing so after the fraud has already been committed.
- Corrective (also referred to as compensating) controls are designed to correct errors, omissions, and unauthorized uses and intrusions once they are detected.
Preventing Misappropriation of Assets
An important component of segregation of duties is to prevent the misappropriation of assets and reduce fraud risk. Below are some examples of best practices for various types of assets:
- Cash Receipt: segregate the receipt of cash/checks and the recording of the journal entry in the accounting system into two roles.
- Accounts Receivable: segregate the responsibilities of recording cash received from customers and providing credit memos to customers. (If one person performs both functions, it creates the opportunity to divert payments from the customer to the employee and then cover the theft with a matching credit to the customer’s account).
- Cash Reconciliation: the individuals who authorize, process, or record cash should not perform the bank reconciliation to the general ledger.
- Inventory: individuals who order goods from the suppliers should not have the ability to log the goods received in the accounting system.
- Payroll: segregate the responsibilities of compiling gross and net pay for payroll, with the responsibilities of verifying the calculation. (If a single individual performs both functions, it allows for the opportunity to increase personal compensation and the compensation of others without authorization. It also provides an opportunity to create a fictitious payee and make corresponding payroll checks).
The Importance of Policies and Procedures
The third key element to look for in your investees is well-established policies and procedures. Make sure that any company you consider acquiring has basic policies and procedures in place, such as Delegation of Authority (DOA).
The DOA is a policy where the executive team delegates authority to the management of the company. Individuals should be considered appropriate to fulfill delegated roles and responsibilities. The DOA should be reviewed at least annually. Subsequently, it is important to ensure that the DOA is being followed, and that approvals do not deviate from it. Any such anomalies should be rare and, when they do occur, they need to be reviewed and approved. Constant deviations from the DOA may be a sign that the DOA needs to be restructured.
A second essential policy and procedure is restricted computer and application access. This is to protect sensitive company financials and proprietary data. The company should have a robust control environment and maintain computer logins and password access on a need-to-know basis. Access should only be granted by the owner of the application or system and subsequently logged by the administrator. Now more than ever companies are hiring remote employees. This shift in the dynamic workspace further emphasizes the need for a quality IT controls environment.
How We Can Help
As you prepare your company for future growth, getting an impartial third-party opinion on your internal control environment can be a powerful tool for finding gaps and inefficiencies, and implementing value-added changes.
Our dedicated Public Company teams offer a deep level of industry experience and technical skills. We can help prepare your company for a major capital raise, including going public via an IPO or RTO. Or we can help optimize value for an M&A deal, whether you are buying or selling. Contact us today to access an external, holistic vision focused on helping you grow and succeed