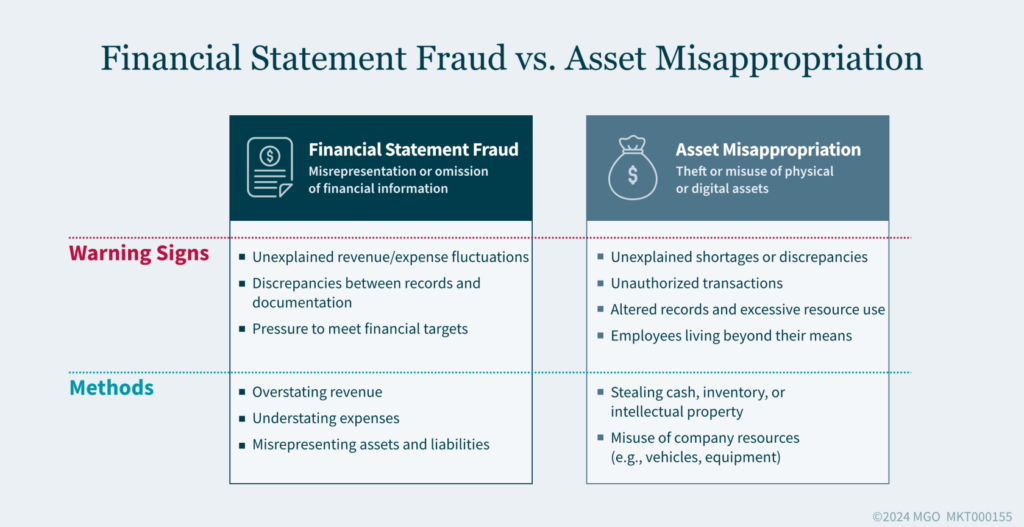
Key Takeaways:
- Watch for unusual behavior patterns among employees.
- Identify abnormalities in transactional data and audit trails.
- Pay attention to whistleblower complaints and tips.
~
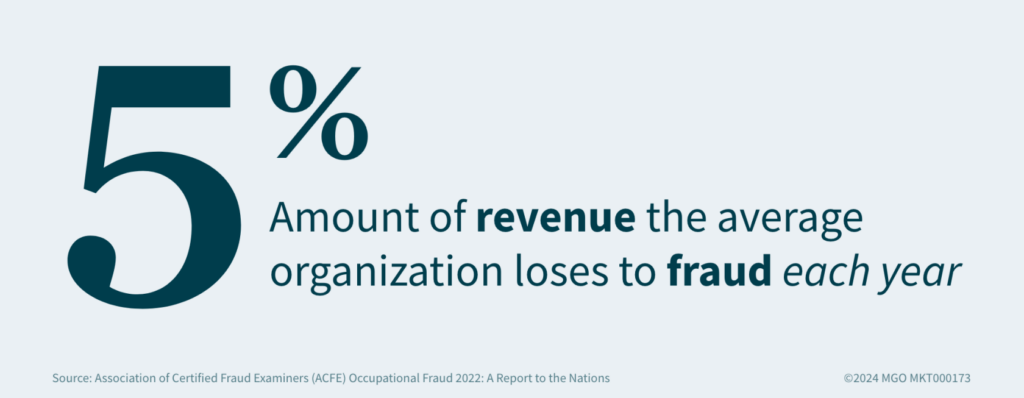
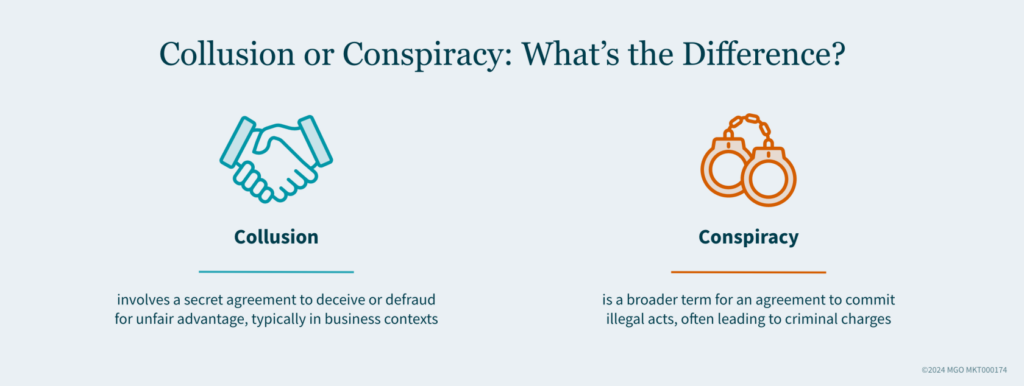
Collusion and conspiracy are serious threats that can undermine your business. Employees working together to deceive others can gain unfair advantages or harm the organization. To safeguard your business, it is crucial to recognize warning signs and implement proactive measures.
Signs of Collusion and Conspiracy
Keep an eye open for these red flags to protect your business:
1. Suspicious Behavior
Be alert to suspicious behaviors among employees. Frequent communication with external parties, secret meetings, or shared access to sensitive information can indicate collusion. These patterns often signal an intent to deceive or manipulate.
2. Unusual Patterns
Be mindful of any unusual patterns that may indicate fraudulent activities. Look for abnormalities in transactional data or audit trails. Missing documentation, altered records, or gaps in the chain of custody are warning signs. These irregularities can conceal fraudulent activities and hinder detection.
3. Changes in Relationships
Pay attention to sudden changes in employee relationships. New alliances between previously unrelated individuals or departments can indicate collusion. These shifts often aim to facilitate deceptive schemes. Businesses should be aware of these changes and investigate any unusual alliances that may form within their teams.
Proactive Measures to Prevent Fraud
Take these actions to defend your organization against the threats of collusion and conspiracy:
1. Evaluate Internal Controls
A lack of segregation of duties or internal controls can enable collusion. When employees can bypass checks and balances, they can perpetrate fraud schemes without detection. Strong internal controls are essential for preventing such activities. Evaluate your company’s internal controls to ensure duties are appropriately segregated and checks are in place.
2. Promote Whistleblower Policies
Take whistleblower complaints, tips, or allegations seriously. Reports of suspected fraudulent activities can provide critical insights. Encouraging a culture of transparency and accountability helps uncover and address collusion. Companies need to establish and promote effective whistleblower policies to ensure employees feel safe reporting suspicious behavior.
3. Review Data and Audit Trails
Your business should regularly review data and audit trails to identify and address any discrepancies promptly. By keeping a close watch on transactional data, you can detect irregularities early and take corrective actions to prevent fraud.
Strengthening Your Organization Against Internal Threats
Collusion and conspiracy pose significant risks, but vigilance and proactive measures can mitigate them. Recognizing red flags, strengthening internal controls, and fostering a culture of trust and ethical behavior help maintain your organization’s integrity. By being mindful of these behaviors, you can strengthen your company’s defenses against fraud and pave the path for long-term success.
How MGO Can Help
MGO provides the resources and experience to effectively address fraud, collusion, and conspiracy. With services including risk assessments, forensic accounting, policy development, and staff training, we can help you identify vulnerabilities, maintain compliance, and establish strong preventive measures.
Learn more about how MGO can support your business at MGO Fraud and Litigation Support.
This is the final article in our ongoing fraud series, “Alert Signals: Uncovering the Spectrum of Fraud,” aimed at educating businesses on identifying and preventing fraudulent activities. Read the previous articles in the series now: