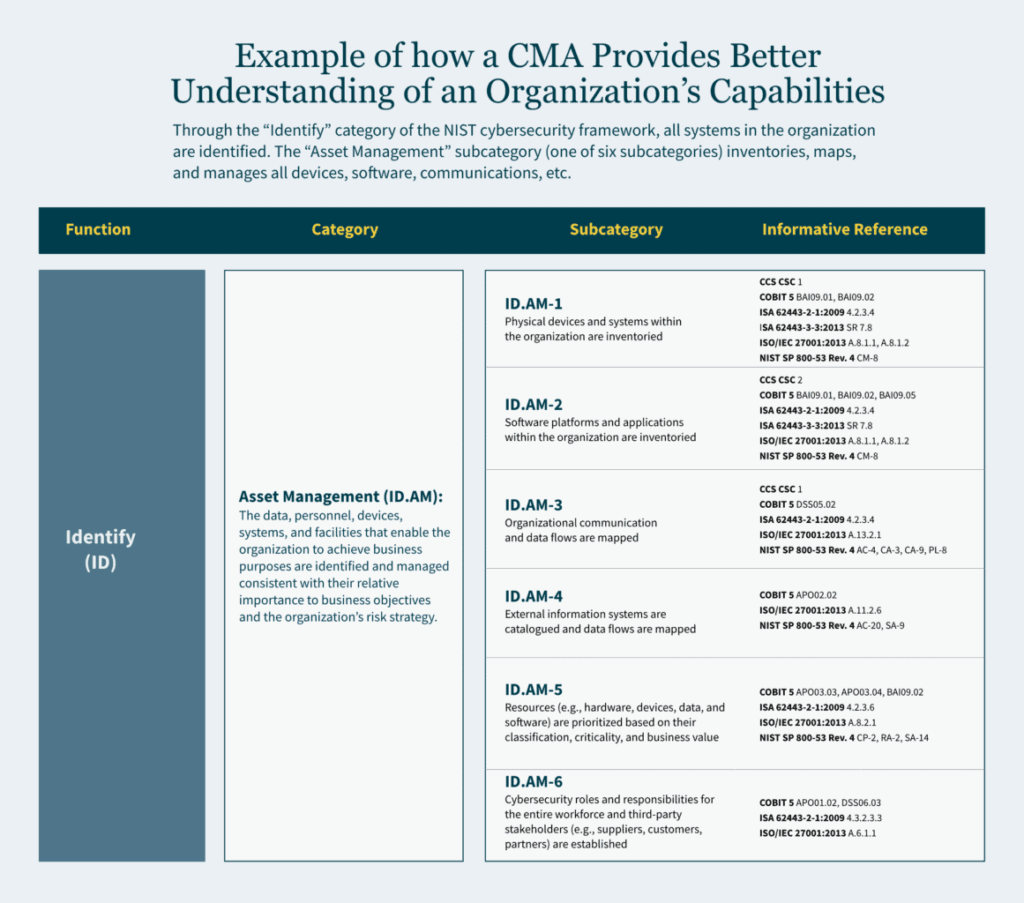
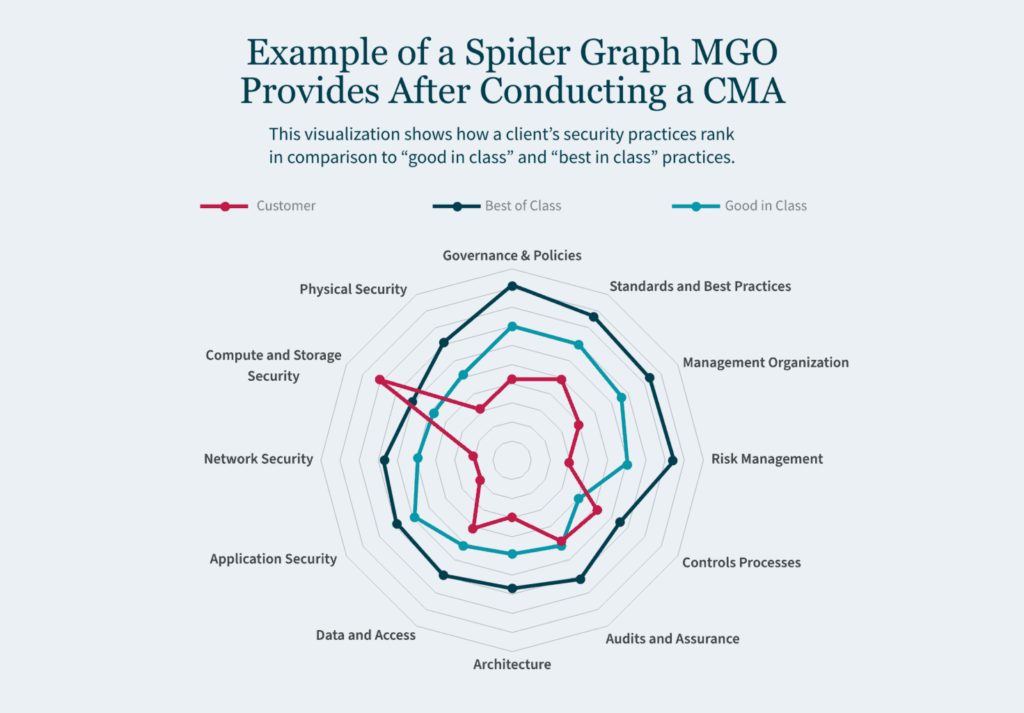
Key Takeaways:
- New SEC cybersecurity rules require public companies to disclose material cybersecurity incidents, risk management processes, and governance.
- Determining “materiality” of cyber incidents for disclosure is challenging and requires close collaboration between CISOs providing technical context and CFOs/executives making final determinations.
- To comply, companies should take steps such as designating accountable leadership, adding specialized cybersecurity knowledge, and updating financial processes.
~
For years, chief financial officers (CFOs) could afford to be removed from the daily cybersecurity efforts led by chief information security officers (CISOs). But, with new Securities and Exchange Commission (SEC) cybersecurity rules, those days are gone.
Adopted on July 26, 2023, the SEC’s “Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure” rules recognize cyber incidents can significantly impact public companies’ operations, finances, and reputations. The requirements push companies to be more transparent and accountable about cybersecurity.
While compliance with these rules falls squarely on publicly traded organizations, the impact extends to private-owned companies as well. If your company is a vendor or partner to public firms, you can expect inquiries and audits to verify you meet their security standards. Liabilities and risks permeate the entire supply chain.
SEC Cybersecurity Disclosure Requirements
If you are a public company, what do you need to report under the new rules? Here are the main requirements:
Cybersecurity Incident Disclosure
- Report within four business days of determining the incident is “material”
- Describe the nature, scope, timing, and impacts (or potential impacts)
- Note any undetermined details at time of filing
- Compliance required for SEC registrants as of December 18, 2023; smaller reporting companies (SRCs) have until June 15, 2024, to comply
Annual Risk Management & Strategy Disclosure
- Outline processes to identify, assess, and manage material cyber risks
- Explain how these processes integrate with overall risk governance
- Detail impacts from previous material incidents
- Disclose use of third-party security consultants/auditors and procedures
- Compliance required for all registrants (including SRCs) beginning with annual reports for fiscal years ending on or after December 15, 2023
Annual Governance Disclosure
- Describe board oversight and committee responsibilities for cyber risk
- Identify management roles accountable for cybersecurity programs
- Specify escalation protocols to board/committees on cyber issues
- Compliance required for all registrants for fiscal years ending on or after December 15, 2023
Determining Cybersecurity “Materiality”
A central tenet of the SEC guidelines is the “materiality” concept regarding incident reporting. Essentially, cybersecurity events are considered “material” and require disclosure if they could sway investment decisions or shareholder votes. Think of materiality as anything significant enough to concern your board and executive team.
The tricky part is that materiality determinations do not solely rest with technology and security leaders. Corporate officers and boards make the ultimate call, despite often lacking full context into security event ramifications on financials and operations. Bridging this disconnect through close CISO collaboration is critical to set appropriate disclosure thresholds aligned with your company’s true risk profile. Ideally, final decisions should also be independently verified by an outside, nonbiased service provider.
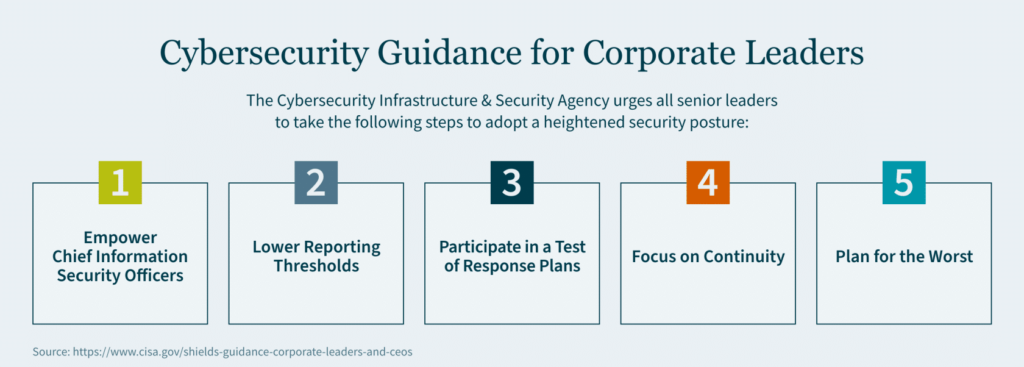
The SEC final rule also makes extensive (more than 40) references to “third party” impacts. A breach or attack affecting a key vendor could very well represent a material event for your organization that necessitates SEC disclosure. Do not let third-party cybersecurity shortcomings undermine compliance.
Best Practices to Comply with New SEC Cybersecurity Rules
While no one-size-fits all checklist exists, your company and relevant vendors should consider these best practices on the path to cybersecurity rule compliance:
1. Designate Accountable Leadership
Empower specific business leaders as security program owners, not just technical teams. These individuals need to establish clear reporting and communication between security operations and the board/c-suite. Executive working sessions focused on cybersecurity scenario planning are also advised.
2. Add Cybersecurity Knowledge
The rules do not explicitly require it, but it is wise to have dedicated cybersecurity oversight at the board level. Bringing in third-party advisors can help boards understand cyber responsibilities and implement improved processes. This knowledge is often lacking today despite its importance.
3. Update Financial Processes
The speedy 8-K cybersecurity incident reporting necessitates updates to disclosure management procedures. Public companies should already have 8-K drafting processes, so adjusting for cyber specifics presents a modest lift. The key is removing bottlenecks to rapidly describe incident details.
4. Dedicate Compliance Resources
CISOs in many companies oversee skeletal teams lacking the bandwidth for major initiatives like interpreting new regulations, implementing new disclosures processes, conducting risk assessments, and more. Ensure your team has the resources needed to achieve compliance.
5. Build Cybersecurity Culture
Equip your leadership team, board, and financial executives with a comprehensive understanding of cyber risks and disclosure nuances. Implement ongoing education and guidance programs to keep them well-versed in cybersecurity threats, response procedures, and the latest developments in the field.
How MGO Can Expedite Your Compliance Journey
The SEC cybersecurity rules are a wake-up call to take cyber preparedness as seriously as any other existential risk to your organization. Let our team of security, financial, and regulatory professionals guide you toward proactive, comprehensive compliance. Reach out today to discuss your roadmap.