Key Takeaways:
- IT operational assessments help Tribal nations and gaming enterprises by enhancing efficiency, security, compliance, and overall business performance.
- Tribal nations can use this 10-question checklist to evaluate current IT practices; identify areas to improve security, compliance, and risk management; and guide future strategic planning and decision-making.
~
Your Tribal nation and its gaming enterprises demand robust and secure information technology (IT) systems. IT operational assessments can significantly contribute to the overall success and sustainability of your property — helping you identify vulnerabilities, optimize systems, verify compliance, and enhance guest experiences.
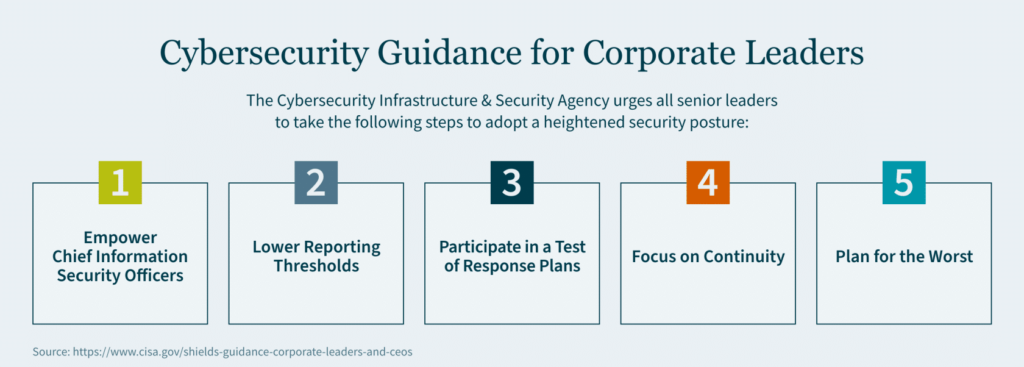
Checklist: 10 Key IT Questions You Should Be Asking
Understanding the importance of IT assessments for your Tribal nation and gaming entities begins with asking these questions:
1. How can we identify potential vulnerabilities in our technology?
Conducting thorough evaluations of your systems, networks, applications, and data assets helps to pinpoint security weaknesses and potential risk within your systems before they can be exploited. Regular assessments help improve defenses against cyberattacks, fraud, and data breaches.
2. What steps should we take to enhance our security posture?
By evaluating the current IT infrastructure, you can identify outdated or inefficient systems and processes that need upgrading or replacement. Streamlining processes through better technology integration can lead to more efficient operations, reducing downtime and increasing productivity. By enhancing your cybersecurity, you safeguard critical data and increase stakeholder confidence.
3. How can we achieve regulatory compliance in our Tribal gaming and business operations?
Maintaining compliance with industry standards and regulatory requirements, such as the Payment Card Industry Data Security Standard (PCI DSS), Gramm-Leach-Bliley Act (GLBA), and other relevant security frameworks, can provide a roadmap to identify risk while upgrading and optimizing IT systems.
4. What strategies should we use to manage risks effectively?
Prioritizing risks based on their potential impact is essential for effective risk management. Allocating resources efficiently to address the most critical threats allows for a comprehensive risk management strategy tailored to the unique needs of your Tribal nation and its gaming entities. This proactive approach helps mitigate potential risks before they become significant issues.
5. How can we support a disaster recovery and business continuity plan?
Continuous gaming and business activities play a pivotal role in the success and reputation of your Tribal entity. Preserving the integrity and availability of your IT systems is indispensable in shielding your operations from potential disruptions. By building a plan, your organization will be able to handle IT incidents efficiently and recover swiftly when challenges arise.
6. What methods can we use to review and update our IT policies and procedures effectively?
Evaluating your current IT policies and procedures for comprehensiveness and relevance keeps them effective. Updating your policies to reflect the latest industry standards and regulatory changes keeps them applicable. And facilitating enforcement and adherence minimizes the risk of IT-related incidents and enhances your overall security.
7. How can we prevent unauthorized access to sensitive data and systems?
Reviewing user access rights, privileges, and authentication mechanisms is essential for preventing unauthorized access to sensitive data and systems. Also, by implementing a robust third-party vendor evaluation process and access controls, you can help mitigate the risk of data breaches and protect valuable information. This process is critical for maintaining the security of your Tribal nation operations and gaming entities.
8. What actions are necessary to secure our network architecture?
To identify vulnerabilities in firewalls, intrusion detection and prevention systems (IDPSs), virtual private networks (VPNs), and network segmentation practices, a thorough evaluation of your network architecture, configuration, and security controls is necessary. Addressing these weaknesses enhances your network security and prevents potential points of compromise. A secure network architecture serves as the foundation for a resilient IT infrastructure.
9. How can we protect our data assets?
Maintaining data protection measures such as encryption, data loss prevention (DLP) controls, and backup procedures is vital for the confidentiality, integrity, and availability of sensitive information. By protecting data against unauthorized access, disclosure, or alteration, your organization can safeguard its critical assets and keep your IT systems secure.
10. What measures should we take to prepare for incident response and maintain effective IT operations?
Establishing efficient incident detection, reporting mechanisms, and escalation processes helps minimize damage and reduce recovery time during IT incidents. Being ready for incidents allows your Tribal nation and gaming entities to respond quickly and effectively to any disruptions.

Strengthening Your Tribal Nation with IT Assessments
Regular IT assessments are not just a regulatory requirement but a strategic necessity for your Tribal nation and its gaming entities. By investing in IT assessments, your organization can protect its digital assets, support business continuity, and maintain stakeholder trust. Stay ahead in the digital age by making IT assessments an integral part of your IT strategy.
For more insights and to explore how our IT advisory solutions can fortify your Tribal enterprise’s defenses, visit MGO’s IT Advisory Solutions.